Design and Implementation of Security Code for the Identification and Authentication Process of Electronic Toll Collection System
Main Article Content
Abstract
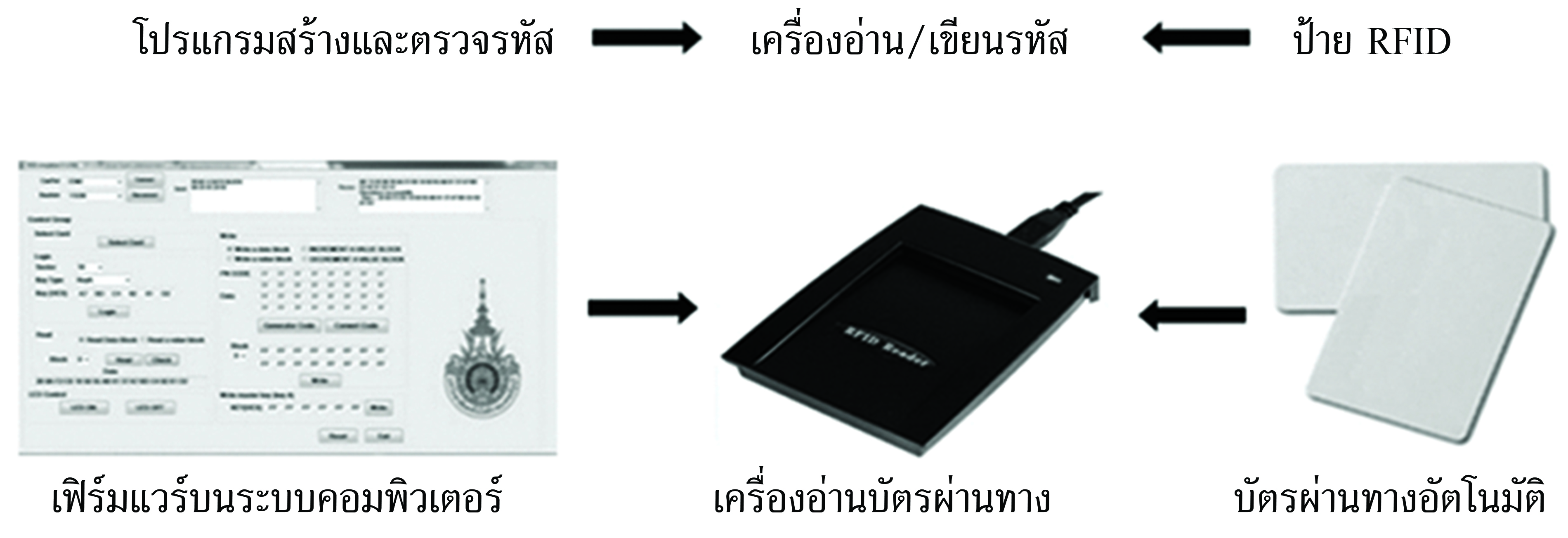
To drive aviation and logistics in Thailand 4.0, it is necessary to use a fast, safe and reliable technology. Radio Frequency Identification (RFID) has adopted into the transportation system in order to identify and authenticate the passengers, vehicles and goods. However, The RFID in transport application still has some problem about the security of ID data. This article presents a method for increasing security in applying RFID to be used in electronic toll collection system. By design and create a security code called Meta_ID and authentication protocol of the RFID reader and tag. Simulate an electronic toll collection system that uses the Meta_ID code and proposed protocol, compared with the original system that uses the fix security code, in the case of 10,000 100,000 and 1,000,000 user’s tags. The simulation results show that the proposed system has a lower probability of hacking success than the original system in all 3 cases. Therefore, concluded that the proposed system has the security performance better than original system.
Article Details
References
[2] Kovinthaweewattana, P., Cheunta, W., Kuankid, S., Baongam, W., and Dinsakul, H. (2009). Radio Frequency Identification (RFID) System. National Science and Technology Development Agency (NSTDA.). (in Thai)
[3] Vaodee, S., Dabbang, P., and Oncheanjit, J. (2010). Anti-Collision Protocol Analysis for Radio Frequency Identification in Logistics Management System. In Proceedings of the Industrial Engineering Network 2010. Ubonratchathani. (in Thai)
[4] Tang Z. (2016). The Design of ETC System Based on RFID and Image Identification. In Proceedings
of the 2016 International Conference on Energy, Power and Electrical Engineering. pp. 236-240. Shenzhen, China. DOI: 10.2991/epee-16.2016.53
[5] Dimitriou, T. (2005). A lightweight RFID Protocol to Protect Against Traceability and Cloning Attacks. In First International Conference on Security and Privacy for Emerging Areas in Communications Networks (SECURECOMM’05). Athens, Greece. pp.59-66. DOI: 10.1109/SECURECOMM.2005.4
[6] Kungpisdan, S. and Metheekul, S. (2009). A Secure Offline Key Generation with Protection Against Key Compromise. In WMSCI 2009: 13th World Multi-Conference on Systemics, Cybernetics and Informatics. 10-13 July 2009, Orlando, Florida. pp. 63-67
[7] Mungmee, S. and Sittichivapak, S. (2009). Development Efficiency of RFID System in Frame ALOHA Communication. Ladkrabang Engineering Journal. Vol. 26, No. 2, pp. 7-12 (in Thai)
[8] Pechto, S. and Kungpisadan, S. (2010). Design and Development of a Lightweight RFID Security Protocol Offering Mutual Authentication. In Proceedings of the 3rd National Conference on Information Technology (NCIT2010). Bangkok. (in Thai)
[9] Lee, Y. K. and Verbauwhede, I. (2005). Secure and Low-Cost RFID Authentication Protocols. Access (4 June 2019). Available (https://www.researchgate.net/publication/250139714_Secure_and_ Low-ost_RFID_Authentication_Protocols)
[10] Khan, G. N. and Moessner, M. B. (2011). Secure Authentication Protocol for RFID Systems. In Proceedings of the 20th International Conference on Computer Communications and Networks (ICCCN). Mauri, Hawaii. pp. 379-384
[11] Peng, P. and Zhao, Y. (2012). Anti-Cloning and Secure RFID Mutual Authentication Protocols. In Proceedings of the 4th IEEE Conference on Broadband Network and Multimedia Technology. Shenzhen, China. pp. 379-384
[12] Dabbang, P. (2003). Performance Analysis of Hybrid DS/SFH SSMA in Multi-user and Multi-rate Environment. M. Eng. Dissertation King Mongkut’s University of Technology Ladkrabang.
[13] GS1 EPC global. (2011). Specification for EPC HF RFID Air Interface. Access (4 June 2019). Available (https://www.gs1.org/sites/default/fi les/docs/epc/epcglobal_hf_2_0_3-standard-20110905r3.pdf)