Intrusion Alert Framework using Semantic Web and Data Mining Approach
Main Article Content
Abstract
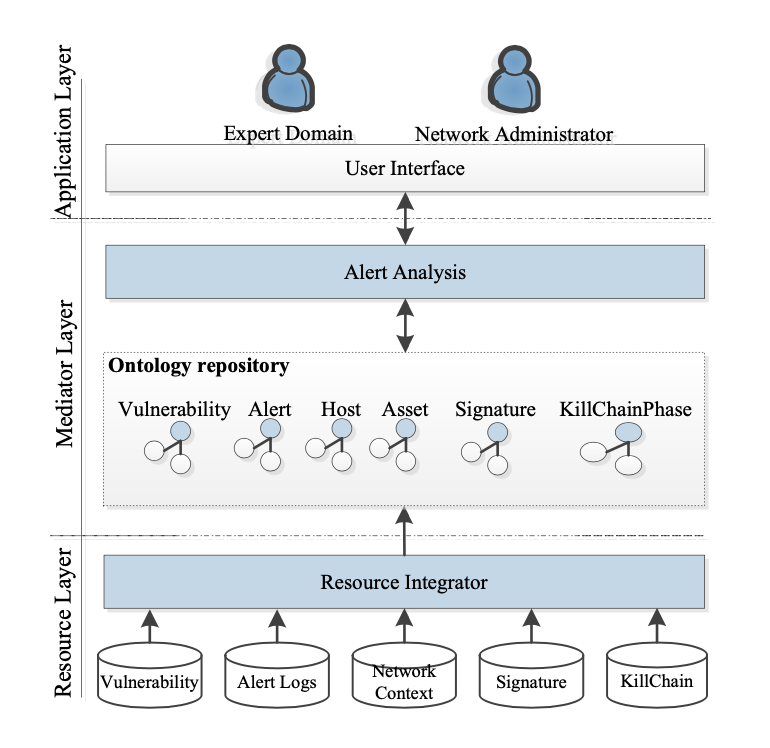
This research proposes a combination of semantic web and datamining approach to examine alert logs and reconstruct attack scenarios that provide crucial evidences to understand about damaging effects, emerged from the attack scenarios. This method extracts information from low-level alerts using ontological knowledge that the candidate attack scenarios are generated using a relationship between alerts, defined by the applied Cyber kill-chain concept. Afterward, Association rule algorithm is applied to mine frequent attack sequential patterns from candidate attack scenarios. Experiments using the DARPA 2000 LLDOS 1.0 dataset indicated that the proposed approach is effective; it reduces the false alerts and extracts a useful information that can solve the direct problems and cut the analysis time. The comparison of the proposed approach with related alert-correlation approaches showed that the approach is more effective than others in particular completeness and soundness.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
All authors need to complete copyright transfer to Journal of Applied Informatics and Technology prior to publication. For more details click this link: https://ph01.tci-thaijo.org/index.php/jait/copyrightlicense
References
Al-Mamory, S.O., & Zhang, H.L. (2007). Scenario discovery using abstracted correlation graph. In the International Conference on Computational Intelligence and Security (CIS) (pp. 702-706). IEEE. https://doi.org/10.1109/CIS.2007.21
Apache. (2017). Apache Jena. Retrieved 20 March 2017, Retrieved from http://jena.apache.org/
Barik, M.S. (2018). AGQL: A query language for attack graph based network vulnerability analysis. In the Fifth International Conference on Emerging Applications of Information Technology (EAIT) (pp. 1-4). https://doi.org/10.1109/EAIT.2018.8470430
Bryant, B.D., & Saiedian, H. (2017). A novel kill-chain framework for remote security log analysis with SIEM software. Computers & Security, 67, 198-210. https://doi.org/10.1016/j.cose.2017.03.003
de Alvarenga, S.C., Barbon, S., Miani, R.S., Cukier, M., & Zarpelão, B.B. (2018). Process mining and hierarchical clustering to help intrusion alert visualization. Computers & Security, 73, 474-491. https://doi.org/10.1016/j.cose.2017.11.021
Debar, H., Curry, D.A., & Feinstein, B.S. (2007). The intrusion detection message exchange format (IDMEF). Request for Comments (Experimental).
García, V., Mollineda, R.A., & Sánchez, J.S. (2008). On the k-NN performance in a challenging scenario of imbalance and overlapping. Pattern Analysis and Applications, 11, 269-280. https://doi.org/10.1007/s10044-007-0087-5
Hahn, A., Thomas, R.K., Lozano, I., & Cardenas, A. (2015). A multi-layered and kill-chain based security analysis framework for cyber-physical systems. International Journal of Critical Infrastructure Protection, 11, 39-50. https://doi.org/10.1016/j.ijcip.2015.08.003
Jungja, K., Ceong, H., & Yonggwan, W. (2009). Weighted association rule mining for item groups with different properties and risk assessment for networked systems. IEICE TRANSACTIONS on Information and Systems, 92(1), 10-15.
Li, W., & Tian, S. (2008). XSWRL, an extended semantic web rule language. In the Intelligent Information Technology Application (IITA) (pp. 437-441). IEEE. https://doi.org/10.1109/IITA.2008.411
Li, W., & Tian, S. (2010). An ontology-based intrusion alerts correlation system. Expert Systems with Applications, 37(10), 7138-7146. https://doi.org/10.1016/j.eswa.2010.03.068
Li, W., Zhi-tang, L., Dong, L., & Jie, L. (2007). Attack scenario construction with a new sequential mining technique. In the Software Engineering, Artificial Intelligence, Networking, and Parallel/Distributed Computing (SNPD) (pp. 872-877), IEEE. https://doi.org/10.1109/SNPD.2007.395
López, V., Fernández, A., García, S., Palade, V., & Herrera, F. (2013). An insight into classification with imbalanced data: Empirical results and current trends on using data intrinsic characteristics. Information Sciences, 250, 113-141. https://doi.org/10.1016/j.ins.2013.07.007
Martin, L. (2014). Cyber Kill Chain®. Retrieved from http://cyber.lockheedmartin.com/hubfs/Gaining_the_Advantage_Cyber_Kill_Chain.pdf
MIT Lincoln Lab. (2002). DARPA intrusion detection scenario specific datasets. Retrieved from https://www.ll.mit.edu/ideval/data/2000/LLS_DDOS_1.0.html
Ning, P., Cui, Y., & Reeves, D.S. (2002). Constructing attack scenarios through correlation of intrusion alerts. In the 9th ACM Conference on Computer and Communications Security (CCS) (pp. 245-254). ACM. https://doi.org/10.1145/586110.586144
NIST Computer Security Division. (2005). NVD-national vulnerability database. Retrieved from https://nvd.nist.gov
NIST Computer Security Division. (2007). CPE-common platform enumeration. Retrieved from https://nvd.nist.gov/cpe.cfm
NIST Computer Security Division. (2016). CVSS-common vulnerability scoring system. Retrieved from https://nvd.nist.gov/cvss.cfm
Njogu, H.W., Jiawei, L., Kiere, J.N., & Hanyurwimfura, D. (2013). A comprehensive vulnerability based alert management approach for large networks. Future Generation Computer Systems, 29(1), 27-45. https://doi.org/10.1016/j.future.2012.04.001
Ontotext. (2017). Graph DB ™. 7.1. Retrieved from: http://ontotext.com/products/graphdb/
OWASP. (2017). Application security risks-2017, open web application security project (OWASP).
Saad, S., & Traore, I. (2013). Semantic aware attack scenarios reconstruction. Journal of Information Security and Applications, 18(1), 53-67. https://doi.org/10.1016/j.jisa.2013.08.002
Sadighian, A., Fernandez, J.M., Lemay, A., & Zargar, S.T. (2014). ONTIDS: A highly flexible context-aware and ontology-based alert correlation framework. In Danger, L.J., Debbabi, M., Marion, J.-Y., Garcia-Alfaro, J., & Heywood, Z.N. (Eds.), Foundations and Practice of Security: 6th International Symposium (FPS) (pp. 161-177). Springer: Cham.
Snort. (2017). Retrieved from: https://www.snort.org/
The MITRE Corporation. (2006). CVE-common vulnerabilities and exposures. Retrieved from: https://cve.mitre.org/
The MITRE Corporation. (2010). CWE-common weakness enumeration. Retrieved from https://cwe.mitre.org
Yu-Xin, D., Hai-Sen, W., & Qing-Wei, L. (2008). Intrusion scenarios detection based on data mining. In the International Conference on Machine Learning and Cybernetics (ICMLC) (pp. 1293-1297). IEEE. https://doi.org/10.1109/ICMLC.2008.4620604
Yuan, B., Pan, Z., Shi, F., & Li, Z. (2020). An attack path generation methods based on graph database. In the 4th Information Technology, Networking, Electronic and Automation Control Conference (ITNEC) (pp. 1905-1910). IEEE. https://doi.org/10.1109/ITNEC48623.2020.9085039