High-speed Firewall Rule Verification Technique Improves Throughput Performance for IP Version 6
Main Article Content
Abstract
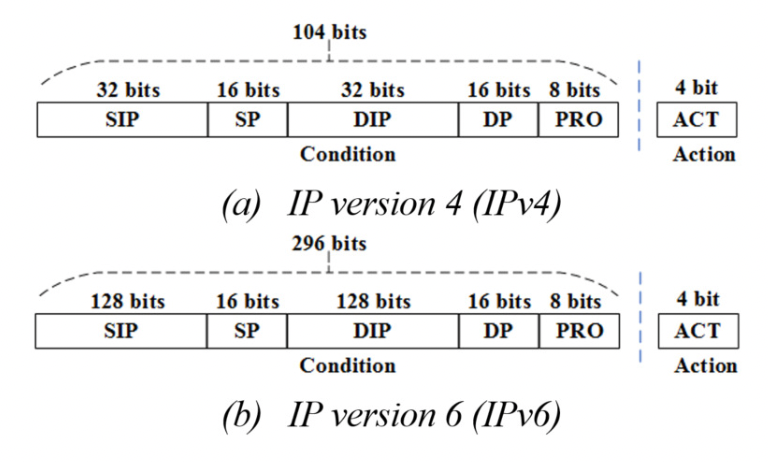
Throughput performance of firewalls depend on the execution speed to verify rules. Internet Protocol Version 6 (IPv6) and IPv4 ruleset memory requirements differ and affect rule access and execution time in a wide range of common firewalls. This paper contributes a high-speed firewall to execute rules for IPv6 with constant O(1) access time, and consumes optimal O(nbit) memory for 64-bit architectures, named FW6 firewall. Results are based on actual performance evaluations in conjunction with other high-speed firewalls (IPSets, IPack, and F3), such as processing time, memory consumption and throughput. Throughput measurements in IPv6 TCP/UDP packet trials (across ruleset and window sizes) show FW6 significantly outperforms IPSets. The trials have shown that FW6 improves throughput performance over IPSets by 0.24% (mean) and 0.21% (median) across all test variables. Nevertheless, the results suggest similarity and a minor performance increase by FW6 over IPSets. In addition, FW6 and IPSets throughputs are similar to IPack and F3 in IPv4 ruleset execution comparisons. As a result, FW6 can be used to replace previous high-speed firewalls.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
References
Suchart Khummanee. (2019, Nov.). IP Packing Technique for High-speed Firewall Rule Verification. Journal of Internet Technology. [Online]. vol. 20, no. 6, pp. 1737-1751. Available: https://jit.ndhu.edu.tw/article/view/2162.
S. Khummanee, P. Chomphuwiset, P. Pruksasri. (2020, Aug.). Decision Making System for Improving Firewall Rule Anomaly Based on Evidence and Behavior. Advances in Science, Technology and Engineering Systems Journal. [Online]. vol. 5, no. 4, pp. 505-515. Available: https://astesj.com/v05/i04/p60/.
S. Khummanee, P. Chomphuwiset, and P. Pruksasri. (2020, Mar.). DSSF: Decision Support System to Detect and Solve Firewall Rule Anomalies based on a Probability Approach. ECTI-CIT. [Online]. vol. 16, no. 1, pp. 56–73. Available: https://ph01.tci-thaijo.org/index.php/ecticit/article/view/246996.
Diekmann, C., Hupel, L., Michaelis, J. et al. (2018, Jan.). Verified iptables Firewall Analysis and Verification. Journal of Automated Reasoning. [Online]. vol. 61, no. 1, pp. 191–242. Available: https://link.springer.com/article/10.1007/s10817-017-9445-1.
S. Khummanee, A. Khumseela and S. Puangpronpitag, “Towards a new design of firewall: Anomaly elimination and fast verifying of firewall rules,” in Proc. JCSSE, 2013, pp. 93-98.
H. Hamed, A. El-Atawy, and E. Al-Shaer. (2006, Oct.). On dynamic optimization of packet matching in high-speed firewalls. IEEE Journal on Selected Areas in Communications. [Online]. vol. 24, no. 10, pp. 1817–1830. Available: https://ieeexplore.ieee.org/document/1705614.
S. Khummanee, P. Songram, and P. Pruksasri. (2022, Mar.). FFF: Fast Firewall Framework to Enhance Rule Verifying over High-speed Networks. ECTI-CIT. [Online]. vol. 16, no. 1, pp. 35–47. Available: https://ph01.tci-thaijo.org/index.php/ecticit/article/view/246990.
J. Kadlecsik. (2021, Apr.). IP set features., [Online]. Available: https://ipset.netfilter.org
S. Khummanee, “The Semantics Loss Tracker of Firewall Rules,” in Proc. IC2IT, 2018, pp. 220-231.
C. Togay, A. Kasif, C. Catal and B. Tekinerdogan.
(2022, Mar.). A Firewall Policy Anomaly Detection Framework for Reliable Network Security. IEEE Transactions on Reliability. [Online]. vol. 71, no. 1, pp. 339-347. Available: https://ieeexplore.ieee.org/document/9478072.
Steve Suehring. (2015, Jan 29). Linux Firewalls: Enhancing Security with nftables and Beyond. (4th ed.) [Online]. Available: https://www.amazon.com/dp/0134000021?tag=uuid10-20.
James Pyles, Jeffrey L. Carrell, Ed Tittel. (2016, Jun 14). Guide to TCP/IP: IPv6 and IPv4. (5th ed.) [Online]. Available: https://www.amazon.com/Guide-TCP-IP-IPv6-IPv4/dp/1305946952.
Amoss, John J.; Minoli, Daniel. (2019, Sep 19). Handbook of IPv4 to IPv6 Transition: Methodologies for Institutional and Corporate Networks. (1st ed.) [Online]. Available: https://www.amazon.com/Handbook-IPv4-IPv6-Transition-Methodologies/dp/0367388057.
R. Hinden. (1998, Jul.). IP Version 6 Addressing Architecture., Cisco Systems. [Online]. Available: https://www.rfc-editor.org/info/rfc2373.
R. Hinden. (2006, Feb.). IP Version 6 Addressing Architecture., IETF. [Online]. Available: https://www.rfc-editor.org/info/rfc4291.
Douglas E. Comer, Internetworking with TCP/IP, London, WC2R 0RL: Pearson, 2013, pp. 185–246.
Behrouz A. Forouzan, TCP/IP Protocol Suite, United States, New York: McGraw Hill, 2009, pp. 375–501.
J. Kadlecsik and G. Psztor. (2020, Dec.). Netfilter performance testing., [Online]. Available: https://people.netfilter.org/kadlec/nftest.pdf.
B. A. Jon Dugan and E. Seth. (2020, June.). IPERF - the ultimate speed test tool for TCP, UDP and SCTP, IPERF testing report 2017. [Online]. Available: https://iperf.fr/.
OpenBSD Journal. (2006, Sep.). PF: Firewall Ruleset Optimization. [Online]. Available: https://undeadly.org/cgi?action=front.