A Privacy Preservation Model for URL Query Strings Based of Local Links Based on Temporary Tables
Main Article Content
Abstract
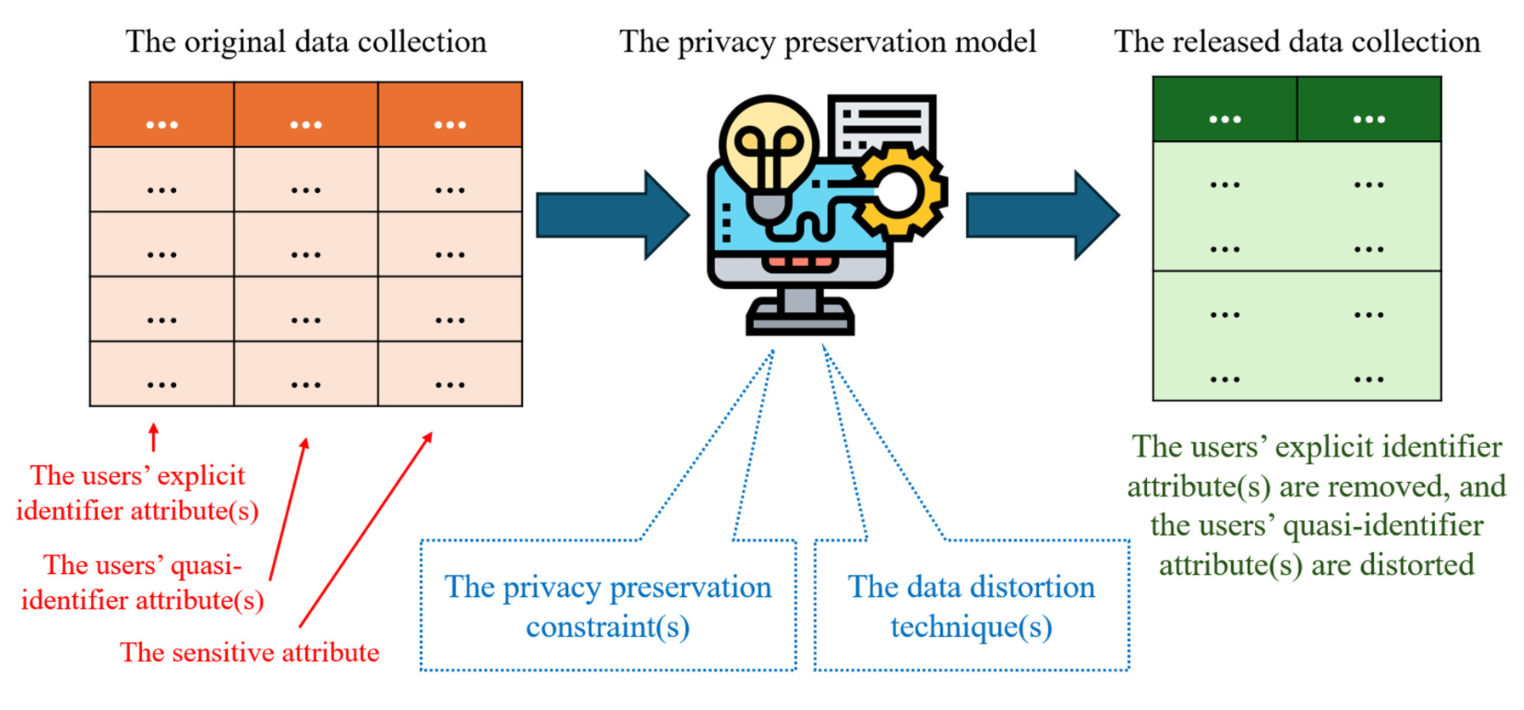
The URL (Uniform Resource Locator) is a unique identifier for locating a resource online. It generally includes a protocol (e.g., HTTP or HTTPS), a subdomain (e.g., WWW), a domain name, a path or webpage, and parameters in the form of URL query strings (HTTP.GET). The parameters proposed to identify the content of the destination webpage, e.g., the user prole, the user activities, or the details of the specified object. Thus, the destination webpage can pose privacy concerns when made publicly available. To rid these concerns in the local link of websites, a new privacy preservation model is proposed in this work. It is based on a temporary table. Aside from addressing privacy violation issues, a significant aim of the proposed models is to maintain the data utility as much as possible. Furthermore, the proposed model is evaluated by using extensive experiments. The experimental results show that the proposed model is an effective privacy preservation model that can be used to address privacy violation issues in URL query strings.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
References
Y. Huang, M. Milani and F. Chiang, “Privacy aware data cleaning-as-a-service,” Information Systems, vol. 94, p. 101608, 2020.
M. Guerriero, D. A. Tamburri and E. Di Nitto, “Defining, Enforcing and Checking Privacy Policies In Data-Intensive Applications,” 2018 IEEE/ACM 13th International Symposium on Software Engineering for Adaptive and Self Managing Systems (SEAMS), Gothenburg, Sweden, pp. 172-182, 2018.
G. A. Afzali and S. Mohammadi, “Privacy preserving big data mining: association rule hiding using fuzzy logic approach,” IET Information Security, vol. 12, no. 1, pp. 15-24, 2018.
S. Riyana and N. Riyana, “Achieving anonymization constraints in high-dimensional data publishing based on local and global data suppressions,” SN Computer Science, vol. 3, no. 3, 2022.
U. Erlingsson, V. Feldman, I. Mironov, A. Raghunathan, K. Talwar and A. Thakurta, “Amplification by shuffling: From local to central differential privacy via anonymity,” in Proceedings of the Thirtieth Annual ACM-SIAM Symposium on Discrete Algorithms, pp. 2468- 2479, 2019.
V. Balcer, A. Cheu, M. Joseph and J. Mao, “Connecting robust shuffle privacy and pan privacy,” in Proceedings of the 2021 ACM-SIAM Symposium on Discrete Algorithms (SODA), pp. 2384-2403, 2021.
D. Rankin, M. Black, R. Bond, J. Wallace, M. Mulvenna and G. Epelde, “Reliability of supervised machine learning using synthetic data in health care: Model to preserve privacy for data sharing,” JMIR medical informatics, vol. 8, no. 7, e18910, 2020.
L. Yao, Z. Chen, X. Wang, D. Liu and G. Wu, “Sensitive Label Privacy Preservation with Anatomization for Data Publishing,” in IEEE Transactions on Dependable and Secure Computing, vol. 18, no. 2, pp. 904-917, 1 March-April 2021.
D. Slijepˇcevi´c, M. Henzl, L. D. Klausner, T. Dam, P. Kieseberg and M. Zeppelzauer, “k-Anonymity in practice: How generalisation and suppression affect machine learning classifiers,” Computers & Security, vol. 111, p. 102488, 2021.
R. Wei, H. Tian and H. Shen, “Improving k-anonymity based privacy preservation for collaborative filtering,” Computers & Electrical Engineering, vol. 67, pp. 509-519, 2018.
S. Zhang, X. Li, Z. Tan, T. Peng and G. Wang, “A caching and spatial K-anonymity driven privacy enhancement scheme in continuous location-based services,” Future Generation Computer Systems, vol. 94, pp. 40-50, 2019.
A. Machanavajjhala, J. Gehrke, D. Kifer and M. Venkitasubramaniam, “L-diversity: privacy beyond k-anonymity,” 22nd International Conference on Data Engineering (ICDE’06), Atlanta, GA, USA, pp. 24-24, 2006.
N. Li, T. Li and S. Venkatasubramanian, “t-Closeness: Privacy Beyond k-Anonymity and l-Diversity,” 2007 IEEE 23rd International Conference on Data Engineering, Istanbul, Turkey, pp. 106-115, 2007.
L. Yao, X. Wang, X. Wang, H. Hu and G. Wu, “Publishing Sensitive Trajectory Data Under Enhanced l-Diversity Model,” 2019 20th IEEE International Conference on Mobile Data Management (MDM), Hong Kong, China, pp. 160-169, 2019.
M. Xue, P. Kalnis and H. K. Pung, “Location diversity: Enhanced privacy protection in location based services,” Location and Context Awareness, vol. 5561, pp. 70-87, 2009.
H. Zhu, H. -B. Liang, L. Zhao, D. -Y. Peng and L. Xiong, “τ -Safe (l,k)-Diversity Privacy Model for Sequential Publication With High Utility,” in IEEE Access, vol. 7, pp. 687-701, 2019.
B. Meden et al., “Privacy–Enhancing Face Biometrics: A Comprehensive Survey,” in IEEE Transactions on Information Forensics and Security, vol. 16, pp. 4147-4183, 2021.
L. Yao, X. Wang, X. Wang, H. Hu and G. Wu, “Publishing Sensitive Trajectory Data Under Enhanced l-Diversity Model,” 2019 20th IEEE International Conference on Mobile Data Management (MDM), Hong Kong, China, pp. 160-169, 2019.
A. R. Pathak, S. Deshpande and M. Panchal, “A secure framework for file encryption using base64 encoding,” Computing and Network Sustainability, vol. 75, pp. 359-366, 2019.
P. Kalia, D. Bansal and S. Sofat, “Privacy preservation in cloud computing using randomized encoding,” Wireless Personal Communications, vol. 120, pp. 2847-2859, 2021.
J. Kaur, A. Agrawal and R. A. Khan, “Encry fuscation: A model for preserving data and location privacy in fog based IoT scenario,” Journal of King Saud University-Computer and Information Sciences, vol. 34, no. 9, pp. 6808-6817, 2022.
A. G. West and A. J. Aviv, “Measuring Privacy Disclosures in URL Query Strings,” in IEEE Internet Computing, vol. 18, no. 6, pp. 52-59, Nov.-Dec. 2014.
S. Orhpomma, V. Mekthanavanh, S. Soukhavong, N. Homdoung, K. Sasujit and S. Riyana, “Model for Preserving Privacy Data in URL Query Strings,” 2024 10th International Conference on Engineering, Applied Sciences, and Technology (ICEAST), Luang Prabang, Laos, pp. 57-60, 2024.
A. A. Khan, M. Abou El-Ela and M. A. Al-Turaigi, “Current-mode Precision Rectification,” International Journal of Electronics, vol.79, No.2, pp.853-859, 1995.
D. Endo, T. Hiyane, K. Atsuta and S. Kondo, “Fractal Image Compression by the Classification in the Wavelet Transform Domain,” Proceeding of 5th IEEE International Conference on Image Processing (ICIP 98), pp.190-193, 1998.
C. Phongcharoenpanich, “Slot Array Antenna,” D. Eng. dissertation, King Mongkut’s Institute of Technology Ladkrabang, Bangkok, Thailand, pp. 138-145, 2001.