Secure Supply Chain Information Interchange using Distributed Trust Backbone
Main Article Content
Abstract
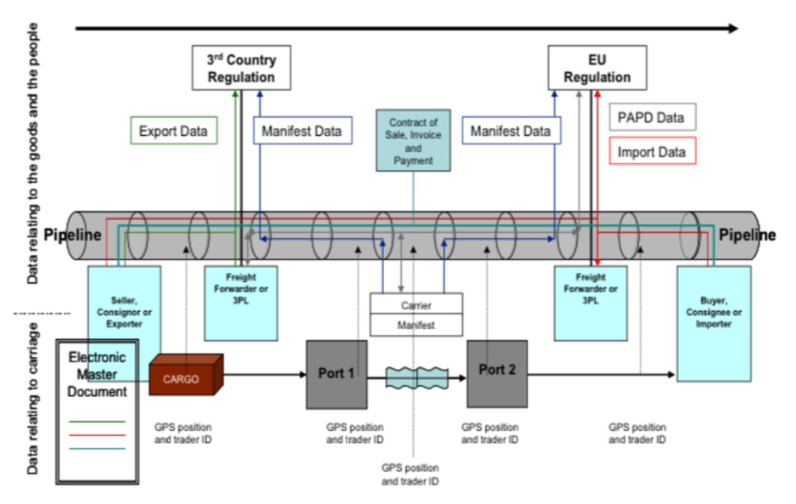
International trade requires transparent visibility of the goods transportation. High-quality data related to containers is essential for container movement across the border speed. However, customs and port authorities face information incorrectness and inconsistency, which are significant determinants that decrease the performance of container clearance in supply chain activities. The Seamless Integrated Data Pipeline principle has been proposed to overcome the mentioned data quality shortcomings and enhance supply chain visibility. Based on the Data Pipeline idea, we proposed the Distributed Trust Backbone (DTB) as a model of secure information exchange between parties within the supply chain activity. However, the supply chain data is highly dynamic. Access control on dynamic resources is the key to enabling secure data exchange and clear visibility. We take this challenge up in this paper. We propose an access control mechanism based on the supply chain Data Pipeline concept and apply it to the DTB model. The elaboration on the concrete detail of the system is presented in this paper. The prototype has been developed and performed in the simulation tests. It reduces 58% of requesting data for supply chain activities. The results of the experiments show that our proposed method performs 100% access control to data with BigO(1) accessing the Access Control List. It can ensure that the information for decision-making in the supply chain is of high quality. The supply chain visibility is clearer and speeds up a modern information exchange system of supply chains.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
References
D. Hesketh, “Weaknesses in the supply chain: Who packed the box?,” World Customs Journal, vol. 4, no. 2, pp. 3-20, 2010.
Y.-H. Tan, N. Bj¨orn-Andersen, S. Klein and B. Rukanova, Accelerating Global Supply Chains with IT-Innovation: ITAIDE Tools and Methods, Springer, 2014, pp.379.
E. V. Stijn et al., “The Data Pipeline,” Global Trade Facilitation Conference 2011Connecting International Trade:Single Windows and Supply Chains in the Next Decade, 2011.
P. Pruksasri, J. V. D. Berg and S. Keretho, “Accountability in Single Window systems using an Internal Certificate Authority: A case study on Thailand’s National Single Window system,” in Proceeding of the 5th IADIS Multiconference on computer science and information systems, pp. 129-136, 2011.
UNECE, “United Nations rules for electronic data interchange for administration, commerce, and transport,” Accessed: 2023. [Online.] Available: https://unece.org/trade/uncefact/unedifact/part-4-rules-electronic-data-interchange-administration-commerce-and-transport
S. Keretho, “UNESCAP High-level ExpertMeeting on “Reduction Poverty by Promoting Industrial Development through Trade Facilitation”,” ASEAN single window initiative and Thailand’s case experience for trade facilitation enhancement, 2010.
UNECE. Recommendation No. 18 Facilitation Measures Related to International Trade Procedures. (2023). Accessed: 2024. [Online]. Available: https://unece.org/trade/uncefact/introducing-unedifact
A. K. Y. Ng, “Port Security and the Competitiveness of Short-Sea Shipping in Europe: Implications and Challenges,” in Risk Management in Port Operations, Logistics, and Supply Chain Security. 1st ed., ImprintInforma Law from Routledge, 2007, pp.1-20.
D. Hesketh, “Seamless electronic data and logistics pipelines shift focus from import declarations to the start of commercial transactions,” World Customs Journal, vol. 3, no. 1, pp. 27-32, 2009.
W. Hofman, “Supply Chain Visibility with Linked Open Data for Supply Chain Risk Analysis,” 1st Workshop on IT Innovations Enabling Seamless and Secure Supply Chains Delft, The Netherlands, pp. 77-78, 2011.
M. V. Oosterhout , M. Zielinski , Y-H Tan, “Inventory of flows & processes in the port,” Virtuele Haven deliverable, 2D1a, 2000.
P. Pruksasri, J. V. D. Berg, W. Hofman and S. Daskapan, “Multi-level access control in the data pipeline of the international supply chain system,” Innovation in the High-Tech Economy, pp. 79–90, 2013.
B. Rukanova, S. Henningsson, H. Henriksen and Y.-H. Tan, “Digital trade infrastructures: a framework for analysis,” Complex systems informatics and modeling quarterly, no. 14, 2018.
B. Rukanova, Y.-H. Tan, R. Huiden, A. Ravulakollu, A. Grainger and F. Heijmann, “A framework for voluntary business government information sharing,” Government Information Quarterly, vol. 37, no. 4, p.101501, 2020.
S. Samonas and D. Coss, “The CIA Strikes Back: Redefining Confidentiality, Integrity and Availability in Security,” Journal of Information System Security, vol. 10, no. 3, pp. 21-45, 2014.
G. Tejpal, R.K. Garg and A. Sachdeva, “Trust among supply chain partners: a review,” Measuring Business Excellence, vol. 17, no. 1, pp. 51-71, 2013.
S. Daskapan, MEDUSA: Survivable information security in critical infrastructures, S. Daskapan, 2005.
H. Eertink, B. Hulsebosch and G. Lenzini, “STORK-eID; Secure Identity Across Borders Linked. Dutch Ministry of the Interior and Kingdom Relations,” Competitiveness and Innovation Framework Programme ICT Policy Support Programme (ICT PSP), Towards pan-European recognition of electronic IDs (eIDs), 2009.
W. Hofman, H. Bastiaansen, J. V. D. Berg and P. Pruksasri, “A platform for secure, safe, and sustainable logistics,” in Proceedings of the eFreight 2012 Conference, pp. 9-10, 2012.
P. Pruksasri, J. van den Berg and W. Hofman, “Global monitoring of dynamic information systems a case study in the international supply chain,” 2014 International Computer Science and Engineering Conference (ICSEC), Khon Kaen, Thailand, pp. 317-322, 2014.
EJBCA, EJBCA Community - Open-source PKI software. (2024). Accessed: 2024. [Online]. Available: https://www.ejbca.org