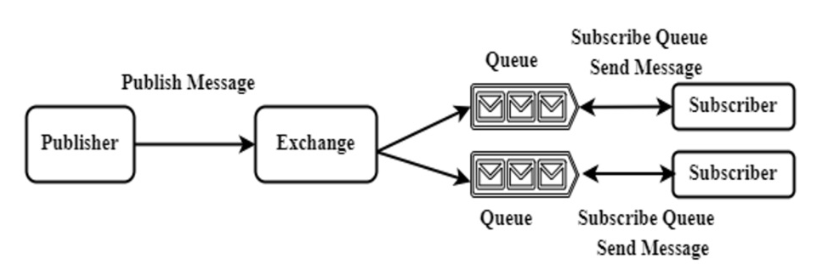
IoT malware detection and Mitigation in AMQP simulated Environment
Main Article Content
Abstract
Internet of Things(IoT) devices are increasing rapidly and providing an infrastructure to connect and share information. Attackers are targeting the IoT network and sending malicious Trac to IoT devices. Devices share large volumes of data, so malware is a security issue. IoT devices work in resource-constrained environments, and malware changes the trac pattern. Due to that, it is a challenging situation to detect malware. An optimized ensemble learning-based approach is applied to detect the malware by analyzing the behavior. Training models employ the NF-BoT-IoT dataset to understand benign and attack trac patterns. Multiple machine learning algorithms were evaluated on a given dataset, and observed that optimized ensemble learning performs best with an outstanding accuracy of 0.9915 and a precision of 0.9937. Another phase of the model mitigates malware by blocking attack IPs of Trac agged as malicious by the detection phase. The model's performance is evaluated in a simulated environment of advanced message queuing protocol(AMQP) using RabbitMQ broker. Future research directions will assist in further research work in enhancing the security of IoT infrastructure.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
References
M. Asam et al., “IoT malware detection architecture using a novel channel boosted and squeezed CNN,” Scientific Reports, vol. 12, no. 15498, 2022.
S. Sasikala and S. Janakiraman, “A Review on Machine Learning-based Malware Detection Techniques for Internet of Things (IoT) Environments,” Wireless Personal Communications, vol. 132, pp. 1961-1974, Aug. 2023.
D. Rani, N. S. Gill and P. Gulia, “Classification of Security Issues and Cyber Attacks in Layered Internet of Things,” Journal of Theoretical and Applied Information Technology, vol. 100, no. 13, pp. 4895–4913, 2022.
R. Praveen and P. Pabitha, “ASK-RAM-IMOT: Autonomous Shared Keys based Remote Authentication Method for Internet of Medical Things Applications,” Wireless Personal Communications, vol. 131, pp. 273-293, 2023.
R. Praveen and P. Pabitha, “Improved Gen-try–Halevi’s fully homomorphic encryption-
based lightweight privacy-preserving scheme for securing medical Internet of Things,” Transactions on Emerging Telecommunications Technologies, vol. 34, no. 4:e4732, 2023.
R. Praveen and P. Pabitha, “A secure, lightweight, uzzy Embedder-based user authenti-
cation scheme for Internet of Medical Things applications,” Journal of Intelligent & Fuzzy Systems, vol. 44, no. 5, pp. 7523–7542, 2023.
U. Khadam, M. M. Iqbal, M. Alruily, M. A. A. Ghamdi, M. Ramzan and S. H. Almotiri,
“Text Data Security and Privacy in the Internet of Things: Threats, Challenges, and Future
Directions,” Wireless Communications and Mobile Computing, vol. 2020, no. 7105625, 2020.
M. Nobakht, R. Javidan and A. Pourebrahimi, “DEMD-IoT: a deep ensemble model for IoT
malware detection using CNNs and network traffic,” Evolving Systems, vol. 14, pp. 46 –477, 2023.
C. Haar and E. Buchmann, “FANE: A Firewall Appliance for the Smart Home,” 2019 Federated Conference on Computer Science and Information Systems (FedCSIS), Leipzig, Germany, pp. 449-458, 2019.
N. Dandotiya, P. Khatri, M. Kumar and S. K. Kachhap, “Sensor-Based Secure Framework for IoT-Based Smart Homes,” in Proceedings of International Conference on Computational Intelligence. Algorithms for Intelligent Systems, Springer, Singapore, pp. 283-290, 2022.
N. Abanmi, H. Kurdi and M. Alzamel, “Dynamic IoT malware detection in Android systems using profile hidden Markov models,” Applied Sciences, vol. 13, no. 1:557, 2022.
A. A. Almazroi and N. Ayub, “Deep learning hybridization for improved malware detection in smart Internet of Things,” Scientific reports, vol. 14, no. 7838, 2024.
A. A. O. Bahashwan and S. Manickam, “A Brief Review of Messaging Protocol Standards for Internet of Things (IoT), vol. 8, no. 1, pp. 1-14, 2018.
F. Iqbal, M. Gohar, H. Alquhayz, S.-J. Koh and J.-G. Choi, “Performance evaluation of AMQP over QUIC in the internet-of-thing networks,” Journal of King Saud University Computer and Information Sciences, vol. 35, no. 4, 1-9, 2023.
R. L´opez-G´omez, L. Panizo and M.-D.-M. Gallardo, “Flextory: Flexible Sof ware Factory of IoT Data Consumers,” Sensors, vol. 24, no. 8:2550, 2024.
G Fu, Y. Zhang and G. Yu, “A Fair Comparison of Message Queuing Systems,” IEEE Access., vol. 9, pp. 421-432, 2021.
S. Dixit and M. Madhu, “Distributing messages using Rabbitmq with advanced message exchanges,” International Journal of Research Studies in Computer Science and Engineering (IJRSCSE), vol. 6, no. 2, pp. 24–28, 2019.
H.-T. Nguyen, D.-H. Nguyen, Q.-D. Ngo, V.- H. Tran and V.-H. Le, “Towards a rooted sub graph classifier for IoT botnet detection,” in Proceedings of the 7th International Conference on Computer and Communications Management, pp. 247-251, 2019.
E. M. Karanja, , S. Masupe and M. G. Jeffrey, “Analysis of Internet of Things malware us-
ing image texture features and machine learning techniques,” Internet of Things, vol. 9, p.100153, 2020.
W. Jung, H. Zhao, M. Sun and G. Zhou, “IoT botnet detection via power consumption modeling,” Smart Health, vol. 15, p. 100103, 2020.
Z. Ma, H. Ge, Y. Liu, M. Zhao and J. Ma, “A Combination Method for Android Malware Detection Based on Control Flow Graphs and Machine Learning Algorithms,” in IEEE Access, vol. 7, pp. 21235-21245, 2019.
Z. Ren, H. Wu, Qian Ning, I. Hussain and B. Chen, “End-to-end malware detection for android IoT devices using deep learning,” Ad Hoc Networks, vol. 101, p. 102098, 2020.
R. M. Arif et al., “A Deep Reinforcement Learning Framework to Evade Black-Box Machine Learning Based IoT Malware Detectors Using GAN-Generated Influential Features,” in IEEE Access, vol. 11, pp. 133717-133729, 2023.
M. Ali, M. Shahroz, M. F. Mushtaq, S. Alfarhood, M. Safran and I. Ashraf, “Hybrid Machine Learning Model for Efficient Botnet Attack Detection in IoT Environment,” in IEEE Access,vol. 12, pp. 40682-40699, 2024.
T. G. Palla and S. Tayeb, “Intelligent Mirai Malware Detection for IoT Nodes,” Electronics, vol. 10, no. 11:1241, May 2021.
A. El-Ghamry, T. Gaber, K. K. Mohammed and A. E. Hassanien, “Optimized and Efficient Image-Based IoT Malware Detection Method,” Electronics. vol. 12, no. 3:708, Jan. 2023.
J. Bhayo, S. A. Shah, S. Hameed, A. Ahmed, J. Nasir and D. Draheim, “Towards a machine learning-based framework for DDOS attack detection in software-defined IoT (SD-IoT) networks,” Engineering Applications of Artificial Intelligence, vol. 123, p. 106432, Aug. 2023.
V. Ravi, T. D. Pham and M. Alazab, “Attention-Based Multidimensional Deep Learning Approach for Cross-Architecture IoMT Malware Detection and Classification in Healthcare
Cyber-Physical Systems,” in IEEE Transactions on Computational Social Systems, vol. 10, no. 4, pp. 1597-1606, Aug. 2023.
F. Khan, M. A. Jan, R. Alturki, M. D. Alshehri, S. T. Shah and A. u. Rehman, “A Secure Ensemble Learning-Based Fog-Cloud Approach for Cyberattack Detection in IoMT,” in IEEE Transactions on Industrial Informatics, vol. 19, no. 10, pp. 10125-10132, Oct. 2023
S. Saravanan and U. M. Balasubramanian, “An Adaptive Scalable Data Pipeline for Multiclass Attack Classification in Large-Scale IoT Networks,” in Big Data Mining and Analytics, vol. 7, no. 2, pp. 500–511, Jun. 2024.
A. Tabassum, A. Erbad, A. Mohamed and M. Guizani, “Privacy-Preserving Distributed IDS Using Incremental Learning for IoT Health Systems,” in IEEE Access, vol. 9, pp. 14271-14283, 2021.
R. Chaganti, A. Mourade, V. Ravi, N. Vemprala, A. Dua and B. Bhushan, “A particle swarm optimization and deep learning approach for intrusion detection system in Internet of Medical Things,” Sustainability, vol.14, no.19, p.12828, Oct. 2022.
M. Sarhan, S. Layeghy and M. Portmann, “Towards a Standard Feature Set for Network Intrusion Detection System Datasets,” Mobile Networks and Applications, vol. 27, no. 1, pp.357-370, 2022.
M. Sarhan, S. Layeghy and M. Portmann, “Evaluating Standard Feature Sets Towards Increased Generalisability and Explainability of ML-Based Network Intrusion Detection,” Big Data Research, vol. 30, p.100359, 2022.
K. A.P. da Costa, J. P. Papa, C. O. Lisboa, R. Munoz and V. H. C. de Albuquerque, “Internet of Things: A survey on machine learning-based intrusion detection approaches,” Computer Networks, vol. 151, pp. 147–157, 2019.