Enhancing Password Storage Through the Integration of Cryptarithmetic Techniques and Hash Functions
Main Article Content
Abstract
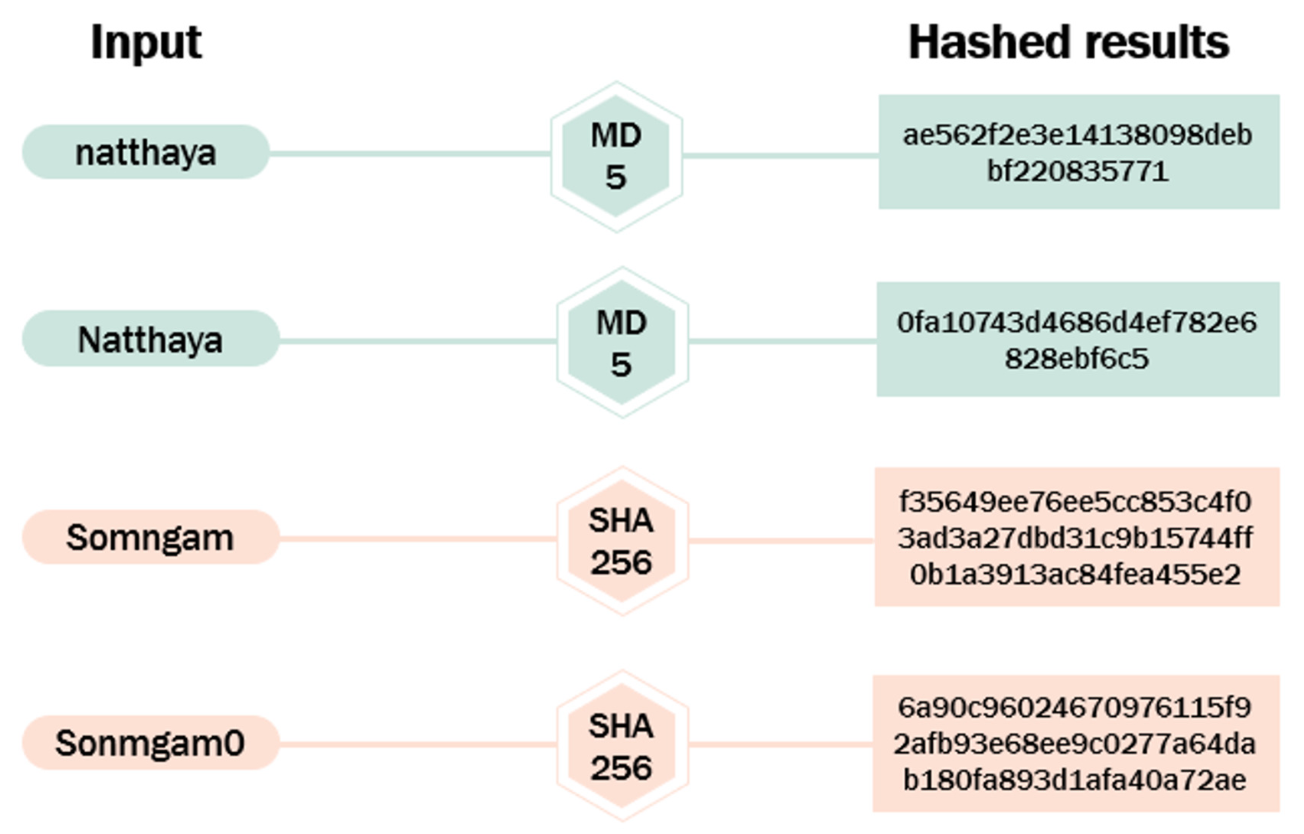
The utilization of internet-based applications oers numerous benefits and significantly enhances the daily lives of individuals. To access these systems, users must provide unique username and password credentials, verifying their identity as the legitimate owners of the data. However, there are instances where unauthorized individuals, including hackers, gain access to these systems by illegitimately exploiting these credentials. This study aims to enhance the system's efficiency by introducing a novel algorithm named Cryptarithmetic_shield. This algorithm combines the Cryptarithmetic technique with a hash function to create a secure encryption system. The research results indicate that password data encrypted using the Cryptarithmetic_shield algorithm, in conjunction with the hash functions MD5, SHA1, SHA256, SHA512, CRC32, and RIPEMD160, effectively prevents decoding from Dictionary attack and Rainbow Table Attack methods, achieving up to 100% effectiveness.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
References
P. S. Rani and S. B. Priya, “Security-Aware and Privacy-Preserving Blockchain Chameleon Hash Functions for Education System,” ECTI-CIT Transactions, vol. 17, no. 2, pp. 225–234, Jun. 2023.
M. N. Hoque, P. Chakraborty and M. H. Seddiqui, “The Challenges and Approaches during the Detection of Cyberbullying Text for Low-resource Language: A Literature Review,” ECTI-CIT Transactions, vol. 17, no. 2, pp. 192–214, Apr. 2023.
C. Mike, “Today’s Information Security Manager,” in CISM Certified Information Security Manager Study Guide, Wiley, pp.1-30, 2022.
S. Barakovic and J. B. Husic, “Cyber hygiene knowledge, awareness, and behavioral practices of university students,” Information Security Journal: A Global Perspective, Taylor & Francis, pp.1-24, 2022.
V. S. Basie and v. S. Rossouw, “Cybersecurity and information security – what goes where?,” Information and Computer Security, vol. 26 No. 1, pp. 2–9, 2018.
A. O. Aljahdalic, S. Banafee and T. Aljohani, “URL filtering using machine learning algorithms,” Information Security Journal: A Global Perspective, Taylor & Francis, 2023.
T. P. Fowdur and S. Hosenally, “A real-time machine learning application for browser extension security monitoring,” Information Security Journal: A Global Perspective, Taylor & Francis, 2022.
H. -M. Ying and N. Kunihiro, “Decryption of Frequent Password Hashes in Rainbow Tables,” 2016 Fourth International Symposium on Computing and Networking (CANDAR), pp. 655-661, 2016.
D. P. Joseph and P. Viswanathan, “SDOT: Secure Hash, Semantic Keyword Extraction, and Dynamic Operator Pattern-Based Three-Tier Forensic Classification Framework,” in IEEE Access, vol. 11, pp. 3291-3306, 2023.
Laatansa, R. Saputra and B. Noranita, “Analysis of GPGPU-Based Brute-Force and Dictionary Attack on SHA-1 Password Hash,” 2019 3rd International Conference on Informatics and Computational Sciences (ICICoS), pp. 1-4, 2019.
L. Boˇsnjak, J. Sreˇs and B. Brumen, “Bruteforce and dictionary attack on hashed real-world passwords,” 2018 41st International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), pp. 1161-1166, 2018.
RG. Rittenhouse and JA. Chaudhry, “A Survey of Alternative Authentication Methods,” International Conference on Recent Advances in Computer Systems (RACS 2015), pp. 179-182, 2015.
I. Neforawati and D. Arnaldy, “Message Digest 5 (MD-5) Decryption Application using Python-Based Dictionary Attack Technique,” 2021 4th International Conference of Computer and Informatics Engineering (IC2IE), pp. 424-428, 2021.
B. Savege, “A Guide to Hash Algorithms,” GIAC Practical Repository, SANS Institute, available at: https://www.giac.org/paper/gsec/2853/guide-hash-algorithms/104822 (accessed 10 September 2022).
B. A. Forouzan, “Cryptography and Network Security,”McGraw-Hill, Inc., pp. 1-480. Available at: http://almuhammadi.com/sultan/books_2020/Forouzan.pdf (accessed 10 September 2022).
R. Rivest, “RFC1321: The MD5 Message-Digest Algorithm,” RFC Editor., available at: https: //dl.acm.org/doi/book/10.17487/RFC1321 (accessed 10 September 2022).
A. A. A B, A. Gupta and S. Ganapathy, “A New Security Mechanism for Secured Communications Using Steganography and CBA,” ECTI-CIT Transactions, vol. 16, no. 4, pp. 460–468, Oct. 2022.
E. M. Michail, G. Athanasiou, F. Theodoridis, A. Gregoriades and E. C. Goutis, “Designand Implementation of Totally-Self Checking SHA1 and SHA-256 Hash Functions Architectures,” Microprocessors and Microsystems, vol. 45, pp. 227-240, 2016.
G. Brose, “Rainbow Tables,” Encyclopedia of Cryptography and Security, Springer, pp. 1021-1022, 2011.
L. Zhang, C. Tan and F. Yu, “An Improved Rainbow Table Attack for Long Passwords,” Procedia Computer Science, vol. 107, pp 47-52, 2017.
B. Bhana and S. V. Flowerday, “Usability of the login authentication process: passphrases and passwords,” Information and computer security, vol. 30 no. 2, pp 280–305, 2022.
J. K ̈avrestad, F. Eriksson and M. Nohlberg, “Understanding passwords a taxonomy of password creation strategies,” Information and computer security, vol. 27, no. 3, pp. 453–467, 2019.
S. Widodo, U. Najati and P. Rahayu, “A Study of Cryptarithmetic problem-solving in elementary school,” Journal of Physics: Conference Series, vol. 1318, pp. 1-8, 2019.
V. Goel, “A comparison of design and nondesign problem spaces,” Artificial Intelligence in Engineering, vol.9, no.1, pp. 53-72, 1994.
B. Averbach and O. Chein, “Problem Solving Through Recreational Mathematics,” Part of: Dover Books on Mathematics, available at: https://archive.org/details/Problem.Solving.Through.Recreational.Mathematics/mode/2up (accessed 10 September 2022).
D. St. P. Barnard, “Adventures in Mathematics,” Pelham Books, London, 2003.
H. E. Dudeney, “The Strand Magazine,” in Strand Magazine, vol.68, pp. 97 and 214, 1924.
S. K. Namdeo, G. S. Kumar and P. Kuyate, “Crypto-Arithmetic Problem using Parallel Genetic Algorithm (PGA),” International Journal of Modern Engineering Research (IJMER), vol.2, no.5, pp. 3275-3280, 2012.
B. Averbach, O. Chein and H. C. Wolfe, “Mathematics: Problem Solving Through Recreational Mathematics,” Physics Today-PHYS TODAY, vol. 34, available at: https://www.researchgate.net/publication/243387866_Mathematics_Problem_SolvingThrough_ Recreational_Mathematics (accessed 10 September 2022).
M. Kraitchik, “Mathematical Recreations,” Dover Publications, Inc. NEW YORK, 2019.
F. Yang, “Solving Cryptarithmetic Puzzles by Logic Programming,” 2020 International Conference on Computational Science and Computational Intelligence (CSCI), IEEE, pp. 1389-1394, 2020.
R. Abbasian and M. Mazloom, “Solving Cryptarithmetic Problems Using Parallel Genetic Algorithm,” 2009 Second International Conference on Computer and Electrical Engineering, IEEE, pp. 308-312, 2009.
A. Minhaz and A. V. Singh, “Solution of a Classical Cryptarithmetic Problem by using parallel genetic algorithm,” Proceedings of 3rd International Conference on Reliability, Infocom Technologies and Optimization, pp. 1-5, 2014.
J. F. Fontanari, “Solving a cryptarithmetic problem using a social learning heuristic,” 2014 IEEE Symposium on Computational Intelligence, Cognitive Algorithms, Mind, and Brain (CCMB), pp. 65-70, 2014.
M. I. Mihailescu and S. L. Nita, “Cryptography and Cryptanalysis in MATLAB,” Creating and Programming Advanced Algorithms, pp. 83–102, 2021.
L. Huang, Q. Yang and W. Zheng, “Online Hashing,” IEEE TRANSACTIONS ON NEURAL NETWORKS AND LEARNING SYSTEMS, vol. 29, no. 6, pp. 2309-2322, 2017.
V. Thing and H. Ying, “Enhanced Dictionary Based Rainbow Table,” Information Security and Privacy Research, Springer, pp.513-524, 2012.
E. I ̇. Tatli, “Cracking More Password Hashes with Patterns,” in IEEE Transactions on Information Forensics and Security, vol. 10, no. 8, pp. 1656-1665, 2015.
H. Kumar, S. Kumar, R. Joseph, D. Kumar, S. K. S. Singh, A. Kumar and P. Kumar, “Rainbow table to crack password using MD5 hashing algorithm,” IEEE Conference on Information and Communication Technologies, pp. 433-439, 2013.
S. Pal, A. Mahanty, A. Pathak, J. Karmakar, H. Mondal and M. Mandal, “A Novel Image Encryption Technique with Four Stage BitInterspersing and A 4D-Hyperchaotic System,” ECTI-CIT Transactions, vol. 17, no. 1, pp. 105–116, Mar. 2023.
A. Almahmoud, E. Damiani and H. Otrok, “Hash-Comb: A Hierarchical DistancePreserving Multi-Hash Data Representation for Collaborative Analytics,” in IEEE Access, vol. 10, pp. 34393-34403, 2022.
J. Polpong and P. Wuttidittachotti, “Authentication and password storing improvement using SXR algorithm with a hash function,” International Journal of Electrical and Computer Engineering (IJECE), vol. 10, no. 6, pp. 6582-6591, 2020.
D. Upadhyay, Gaikwad, M. Zaman and S. Sampalli, “Investigating the Avalanche Effect of Various Cryptographically Secure Hash Functions and Hash-Based Applications,” in IEEE Access, vol. 10, pp. 112472-112486, 2022.
W. Ma, J. Campbell, D. Tran and D. Kleeman, “Password Entropy and Password Quality,” 2010 Fourth International Conference on Network and System Security, pp. 583-587, 2010.
NordPass, “The 200 Most Popular Usernames of All Time,” available at: https://nordpass.com/blog/all-time-most-popular-usernames/ (accessed 10 January 2023).
NordPass, “Top 200 most common passwords,” available at: https://nordpass.com/most-common-passwords-list/ (accessed 10 January 2023).
R. B. Miller, “Response time in man-computer conversational transactions,” The roceedings of the fall joint computer conference, part I, pp. 267-277, 1968.