Image Steganography-based Copyright and Privacy-Protected Image Trading Systems
Main Article Content
Abstract
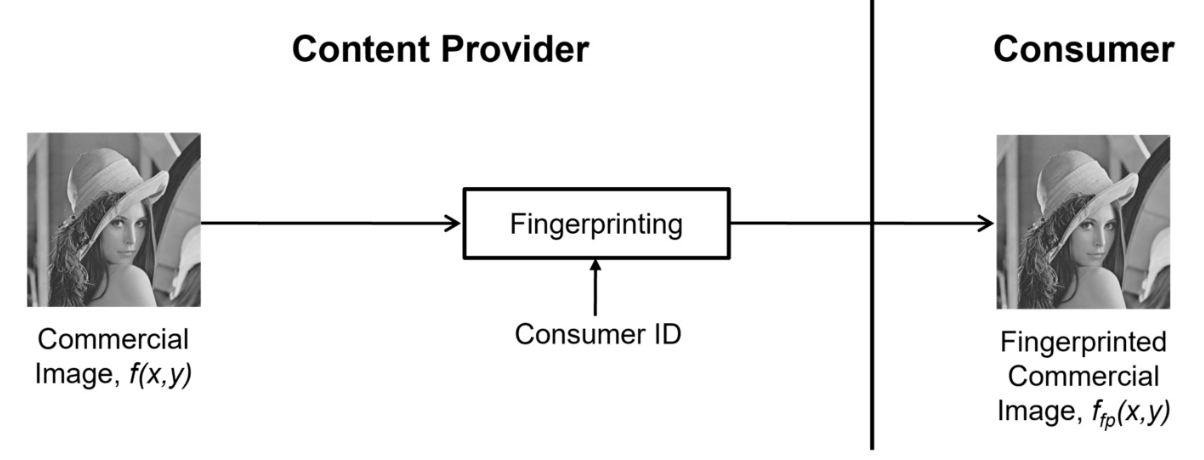
This paper proposes steganography-based copyright- and privacy-protected image trading systems using image transformation, i.e., either discrete cosine transform (DCT) or Hadamard transform (HT). In the systems, there are a content provider (CP), a consumer, the first trusted third party (TTP), and the second TTP. To protect the copyright of the image, the consumer ID is embedded into the amplitude components of the commercial image by the first TTP using the digital fingerprinting technique, and to protect the consumer's privacy against the first TTP and a malicious third party (s), the image steganography is applied to the commercial image by using image transformation. A color dummy image is used instead of a gray dummy image for security purposes. After applying the image transformation to both images, the coefficient signs of the commercial image are replaced by the coefficient signs of the dummy image pixel-by-pixel so that the inversely transformed commercial image looks like the dummy image instead of the commercial image. Once the consumer receives the fingerprinted image from the first TTP and the coefficient signs of the commercial image from the second TTP, the consumer reconstructs the fingerprinted commercial image without losing the hidden fingerprint at all because of the compatibility of the proposed image steganography method and the amplitude-based fingerprinting method. The experimental results confirm that the stego-images generated by the proposed systems do not look suspicious with higher qualities compared with those generated by existing systems. Moreover, the fingerprinted image quality and the correct fingerprint extracting rate have been improved by the proposed systems.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
References
R. L. Lagendijk, Z. Erkin, and M. Barni, “Encrypted signal processing for privacy protection: conveying the utility of homomorphic encryption and multiparty computation,” IEEE Signal Processing Magazine, vol. 30, no. 1, pp. 82-105, Jan. 2012.
M. Kuribayashi, “Recent fingerprinting techniques with cryptographic protocol,” Signal Processing, 2010.
I. J. Cox, M. L. Miller, J. A. Bloom, J. Fridrich, and T. Kalker, Digital watermarking and steganography, 2nd ed., Morgan Kaufmann Publishers, 2008.
B. Schneier, Applied cryptography: protocols, algorithms, and source code in C, 2nded., John Wiley & Sons, 1996.
Y. Sengoku and H. Hioki, “A model of privacy and copyright-aware image trading system based on adaptive image segmentation and digital watermarking,” Proceeding of 27th International Technical Conference on Circuits/Systems, Computers, and Communications (ITC-CSCC 2012), pp. D-W1-02, 2012.
Y. Sengoku and H. Hioki, “An image segmentation method for privacy and copyright-aware image trading system,” IEICE Technical Report, vol. 111, no. 496, EMM2011-67, pp. 19-24, Mar. 2012.
M. Okada, Y. Okabe, and T. Uehara, “A web-based privacy-secure content trading system for small content providers using semi-blind digital watermarking,” Proceeding of 7th IEEE Consumer Communications & Networking Conference (CCNC 2010), 2010.
S. Liu, M. Fujiyoshi, and H. Kiya, “An image trading system using amplitude-only images for privacy and copyright-protection,” IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, vol. E96-A, pp. 1245-1252, Jun. 2013.
W. Sae-Tang, M. Fujiyoshi, and H. Kiya, “A generation method of amplitude-only images with low intensity ranges,” IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, vol. E96-A, no. 6, pp. 1323-1330, Jun. 2013.
W. Sae-Tang, S. Liu, M. Fujiyoshi, and H. Kiya, “1D Frequency transformation-based amplitude-only images for copyrightand privacy-protection in image trading systems,” ECTI-CIT, vol. 8, No. 2, Nov. 2014.
W. Sae-Tang, M. Fujiyoshi, and H. Kiya, “Evaluation of amplitude-only images for copyrightand privacy-protected image trading systems,” Proceeding of 29th International Technical Conference on Circuits/Systems, Computers, and Communications (ITC-CSCC 2014), pp. 113-116, 2014.
W. Sae-Tang and H. Kiya, “Hadamard transform-based amplitude-only images for image trading systems,” 2016 International Workshop on Advanced Image Technology (IWAIT 2016), pp. 3C.5, 2016.
W. Sae-Tang, M. Fujiyoshi, and H. Kiya, “Encryption-then-compression-based copyrightand privacy-protected image trading system,” 2017 International Conference on Advances in Image Processing (ICAIP 2017), pp. 66-71, 2017.
W. Sae-Tang, M. Fujiyoshi, and H. Kiya, “A new copyright and privacy-protected image trading system using a novel steganography-based visual encryption scheme,” ECTI-EEC, vol. 17, no. 1, pp. 95-107, Feb. 2019.
N. F. Johnson and S. Jajodia, “Exploring steganography: Seeing the unseen,” Computer, vol. 31, no. 2, pp. 26-34, Feb. 1998.
S. Gupta, G. Gujral, and N. Aggarwal, “Enhanced least significant bit algorithm for image steganography,” Int. J. Comput. Eng. Manage., vol. 15, no. 4, pp. 40-42, 2012.
R. J. Mstafa, K. M. Elleithy, and E. Abdelfattah, “A robust and secure video steganography method in DWT-DCT domains based on multiple object tracking and ECC,” IEEE Access, vol. 5, pp. 5354-5365, 2017.
G. Swain, “Very high capacity image steganography technique using quotient value differencing and LSB substitution,” Arabian J. Sci. Eng., vol. 44, no. 4, pp. 2995-3004, Apr. 2019.
A. Qiu, X. Chen, X. Sun, S. Wang, and W. Guo, “Coverless image steganography method based on feature selection,” J. Inf. Hiding Privacy Protection, vol. 1, no. 2, p. 49, 2019.
R. D. Rashid and T. F. Majeed, “Edge based image steganography: Problems and solution,” Proceeding of 2019 International Conference on Communications, Signal Processing, and their Applications (ICCSPA), pp. 1-5, Mar. 2019.
X. Liao, J. Yin, S. Guo, X. Li, and A. K. Sangaiah, “Medical JPEG image steganography based on preserving inter-block dependencies,” Comput. Electr. Eng., vol. 67, pp. 320-329, Apr. 2018.
W. Lu, Y. Xue, Y. Yeung, H. Liu, J. Huang, and Y. Shi, “Secure halftone image steganography based on pixel density transition,” IEEE Trans. Dependable Secure Comput., Aug. 6, 2019.
Y. Zhang, C. Qin, W. Zhang, F. Liu, and X. Luo, “On the fault-tolerant performance for a class of robust image steganography,” Signal Process., vol. 146, pp. 99-111, May 2018.
H. M. Sidqi and M. S. Al-Ani, “Image steganography: Review study,” Proceeding of Int. Conf. Image Process., Comput. Vis., Pattern Recognit. (IPCV), pp. 134-140, 2019.
P. Wu, Y. Yang, and X. Li, “Image-into-image steganography using deep convolutional network,” Proceeding of Pacific Rim Conf. Multi-media. Cham, Switzerland: Springer, pp. 792-802, 2018.
P. Wu, Y. Yang, and X. Li, “StegNet: Mega image steganography capacity with deep convolutional network,” Future Internet, vol. 10, no. 6, p. 54, Jun. 2018.
X. Duan, K. Jia, B. Li, D. Guo, E. Zhang, and C. Qin, “Reversible image steganography scheme based on a U-Net structure,” IEEE Access, vol. 7, pp. 9314-9323, 2019.
T. P. Van, T. H. Dinh, and T. M. Thanh, “Simultaneous convolutional neural network for highly efficient image steganography,” Proceeding of 19th Int. Symp. Commun. Inf. Technol. (ISCIT), pp. 410-415, Sep. 2019.
R. Rahim and S. Nadeem, “End-to-end trained CNN encoder-decoder networks for image steganography,” Proceeding of Eur. Conf. Comput. Vis. (ECCV), pp. 1-6, 2018.
Z. Wang, N. Gao, X. Wang, J. Xiang, and G. Liu, “STNet: A style transformation network for deep image steganography,” Proceeding of Int. Conf. Neural Inf. Process. Cham, Switzerland: Springer, pp. 3-14, 2019.
K. Yang, K. Chen, W. Zhang, and N. Yu, “Provably secure generative steganography based on autoregressive model,” Proceeding of Int. Workshop Digit. Watermarking. Cham, Switzerland: Springer, pp. 55-68, 2018.
R. Zhang, S. Dong, and J. Liu, “Invisible steganography via generative adversarial networks,” Multimedia Tools Appl., vol. 78, no. 7, pp. 8559-8575, Apr. 2019.
S. Islam, A. Nigam, A. Mishra, and S. Kumar, “VStegNET: Video steganography network using spatio-temporal features and microbottleneck,” Proceeding of BMVC, p. 274, Sep. 2019.
I. Goodfellow, J. Pouget-Abadie, M. Mirza, B. Xu, D. Warde-Farley, S. Ozair, A. Courville, and Y. Bengio, “Generative adversarial nets,” Proceeding of Adv. Neural Inf. Process. Syst., pp. 2672-2680, 2014.
D. Volkhonskiy, B. Borisenko, and E. Burnaev, “Generative adversarial networks for image steganography,” Proceeding of ICRL Conf., 2016.
D. Volkhonskiy, I. Nazarov, and E. Burnaev, “Steganographic generative adversarial networks,” Proceeding of 12th Int. Conf. Mach. Vis. (ICMV), vol. 11433, Art. no. 114333M, 2020.
D. J. Im, C. D. Kim, H. Jiang, and R. Memisevic, “Generating images with recurrent adversarial networks,” 2016., arXiv:1602.05110. [Online]. Available: http://arxiv.org/abs/1602.05110
H. Shi, J. Dong, W. Wang, Y. Qian, and X. Zhang, “SSGAN: Secure steganography based on generative adversarial networks,” Proceeding of Pacific Rim Conf. Multimedia. Cham, Switzerland: Springer, pp. 534-544, 2017.
J. Yang, K. Liu, X. Kang, E. K. Wong, and Y.-Q. Shi, “Spatial image steganography based on generative adversarial network,” 2018., arXiv:1804.07939. [Online]. Available: http://arxiv.org/abs/1804.07939
J. Yang, D. Ruan, J. Huang, X. Kang, and Y.-Q. Shi, “An embedding cost learning framework using GAN,” IEEE Trans. Inf. Forensics Security, vol. 15, pp. 839-851, 2020.
W. Tang, S. Tan, B. Li, and J. Huang, “Automatic steganographic distortion learning using a generative adversarial network,” IEEE Signal Process. Lett., vol. 24, no. 10, pp. 1547-1551, Oct. 2017.
J. Zhu, R. Kaplan, J. Johnson, and L. Fei-Fei, “Hidden: Hiding data with deep networks,” Proceeding of Eur. Conf. Comput. Vis. (ECCV), pp. 657-672, 2018.
J.-Y. Zhu, T. Park, P. Isola, and A. A. Efros, “Unpaired image-to-image translation using cycle-consistent adversarial networks,” Proceeding of IEEE Int. Conf. Comput. Vis. (ICCV), pp. 2223-2232, Oct. 2017.
A. Odena, C. Olah, and J. Shlens, “Conditional image synthesis with auxiliary classifier GANs,” Proceeding of Int. Conf. Mach. Learn., pp. 2642-2651, 2017.
Z. Zhang, G. Fu, J. Liu, and W. Fu, “Generative information hiding method based on adversarial networks,” Proceeding of Int. Conf. Comput. Eng. Netw. Cham, Switzerland: Springer, pp. 261-270, 2018.
M.-M. Liu, M.-Q. Zhang, J. Liu, Y.-N. Zhang, and Y. Ke, “Coverless information hiding based on generative adversarial networks,” 2017., arXiv:1712.06951. [Online]. Available: http://arxiv.org/abs/1712.06951
X. Duan, H. Song, C. Qin, and M. K. Khan, “Coverless steganography for digital images based on a generative model,” Comput., Mater. Continua, vol. 55, no. 3, pp. 483-493, Jul. 2018.
Z. Wang, N. Gao, X. Wang, X. Qu, and L. Li, “SSteGAN: Self-learning steganography based on generative adversarial networks,” Proceeding of Int. Conf. Neural Inf. Process. Cham, Switzerland: Springer, pp. 253-264, 2018.
R. K. Pradhan, “Does Rayleigh scattering explain the Blueness of Sky?,” Science, vol. 28, no. 31, 2015.
L. Liberti, C. Lavor, N. Maculan, and A. Mucherino, “Euclidean distance geometry and applications,” SIAM review, vol. 56, No. 1, pp. 3-69, 2014.
D. R. I. M. Setiadi, “PSNR vs SSIM: imperceptibility quality assessment for image steganography,” Multimedia Tools and Applications, vol. 80, no. 6, pp. 8423-8444, 2021.
Q. Huynh-Thu and M. Ghanbari, “Scope of validity of PSNR in image/video quality assessment,” Electronics Letters, vol. 44, no. 13, pp. 800-801, 2008.
Q. Huynh-Thu and M. Ghanbari, “The accuracy of PSNR in predicting video quality for different video scenes and frame rates,” Telecommunication Systems, vol. 49, no. 1, pp. 35-48, 2012.