Effective Privacy Preservation Models for Rating Datasets
Main Article Content
Abstract
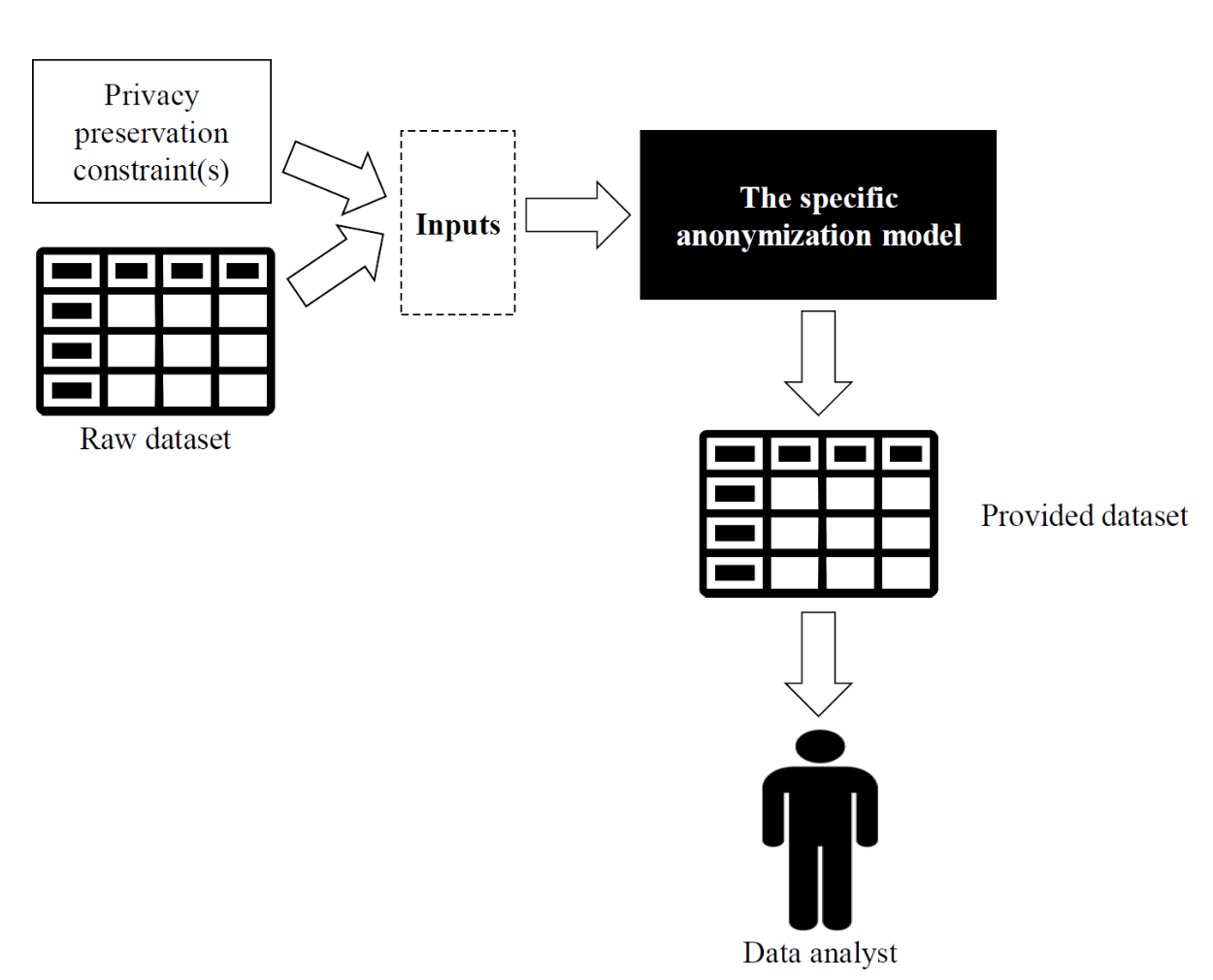
Rating datasets are data collections of user prole tuples that generally include their person-specific data and the preferred level of their interesting artifacts. Generally, rating datasets are generated for use by recommendation methods that are available in real-life systems such as mobile applications, location-based services, e-commerce systems, and websites. Aside from recommendation methods, we can see that rating datasets can further be utilized by data analysts with appropriate business reasons such as improving system policies and constructing business reports. Such a data utilization of rating datasets can lead to privacy violation issues. To address these issues in rating datasets, (lp1 , . . . , lpn )-Privacy is proposed. That is, before rating datasets are utilized by the specified recommendation method and data analysts, the user's unique preferences in rating datasets are generalized by less specific data to be indistinguishable. Moreover, the generalized rating dataset can only be utilized through aggregate query frameworks. Although this privacy preservation model can address privacy violation issues in rating datasets, it still has a serious data utility issue that must be improved. For this reason, a new effective privacy preservation model for rating datasets is proposed in this work. Moreover, we propose practical experiments that can measure the effectiveness of the proposed privacy preservation model. The experimental results show that the proposed privacy preservation model is highly effective.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
References
Bayardo, R.J., Agrawal, R.: Data privacy through optimal k-anonymization. In: 21st International Conference on Data Engineering (ICDE’05), pp. 217–228 (2005). DOI 10.1109/ICDE.2005.42
Calandrino, J.A., Kilzer, A., Narayanan, A., Fel- ten, E.W., Shmatikov, V.: ”you might also like:” privacy risks of collaborative filtering. In: 2011 IEEE Symposium on Security and Privacy, pp. 231–246 (2011). DOI 10.1109/SP.2011.40
Fung, B.C.M., Cao, M., Desai, B.C., Xu, H.: Privacy protection for rfid data. In: Proceedings of the 2009 ACM Symposium on Applied Computing, SAC ’09, pp. 1528–1535. ACM, New York, NY, USA (2009). DOI 10.1145/1529282.1529626
Gal, T., Chen, Z., Gangopadhyay, A.: A privacy protection model for patient data with multiple sensitive attributes. IJISP 2, 28–44 (2008). DOI 10.4018/jisp.2008070103
Ghinita, G., Karras, P., Kalnis, P., Mamoulis, N.: A framework for efficient data anonymization under privacy and accuracy constraints. ACM Trans. Database Syst. 34(2), 9:1–9:47 (2009). DOI 10.1145/1538909.1538911
Harper, F.M., Konstan, J.A.: The movielens datasets: History and context. ACM Trans. Interact. Intell. Syst. 5(4), 19:1–19:19 (2015). DOI 10.1145/2827872
P. Tirelli, N. A. Borghese, F. Pedersini, G. Galassi and R. Oberti, “Automatic monitoring of pest insects traps by Zigbee-based wireless networking of image sensors,” 2011 IEEE International Instrumentation and Measurement Technology Conference, pp. 1-5, 2011.
Li, Z., Ye, X.: Privacy protection on multiple sensitive attributes. In: S. Qing, H. Imai, G. Wang (eds.) Information and Communications Security, pp. 141–152. Springer Berlin Heidelberg, Berlin, Heidelberg (2007)
Linden, G., Smith, B., York, J.: Amazon.com recommendations: item-to-item collaborative filtering. IEEE Internet Computing 7(1), 76–80 (2003). DOI 10.1109/MIC.2003.1167344
Machanavajjhala, A., Kifer, D., Gehrke, J., Venkitasubramaniam, M.: L-diversity: Privacy beyond k-anonymity. ACM Trans. Knowl. Discov. Data 1(1) (2007). DOI 10.1145/1217299.1217302
Ramakrishnan, N., Keller, B.J., Mirza, B.J., Grama, A.Y., Karypis, G.: Privacy risks in recommender systems. IEEE Internet Computing 5(6), 54–62 (2001). DOI 10.1109/4236.968832
Riyana, S.: (lp1 , ... , lpn )-privacy: privacy preservation models for numerical quasi-identifiers and multiple sensitive attributes. J. Ambient Intell. Humaniz. Comput. 12(10), 9713–9729 (2021). DOI 10.1007/s12652-020- 02715-3. URL https://doi.org/10.1007/s12652-020-02715-3
Riyana, S., Harnsamut, N., Soontornphand, T., Natwichai, J.: (k, e)-anonymous for ordinal data. In: 2015 18th International Conference on Network-Based Information Systems, pp. 489– 493 (2015). DOI 10.1109/NBiS.2015.118
Riyana, S., Ito, N., Chaiya, T., Sriwichai, U., Dussadee, N., Chaichana, T., Assawarachan, R., Maneechukate, T., Tantikul, S., Riyana, N.: Pri- vacy threats and privacy preservation techniques for farmer data collections based on data shuffling. ECTI Transactions on Computer and Information Technology (ECTI-CIT) 16(3), 289– 301 (2022)
Riyana, S., Nanthachumphu, S., Riyana, N.: Achieving privacy preservation constraints in missing-value datasets. SN Computer Science 1(4), 1–10 (2020)
Riyana, S., Natwichai, J.: Privacy preservation for recommendation databases. Service Oriented Computing and Applications (2018). DOI 10.1007/s11761-018-0248-y
Riyana, S., Riyana, N.: A privacy preservation model for rfid data-collections is highly secure and more efficient than lkc-privacy. In: The 12th International Conference on Advances in Information Technology, pp. 1–11 (2021)
Riyana, S., Riyana, N.: Achieving anonymization constraints in high-dimensional data publishing based on local and global data suppressions. SN Computer Science 3(1), 1–12 (2022)
Riyana, S., Riyana, N., Nanthachumphu, S.: Enhanced (k,e)-anonymous for categorical data. In: Proceedings of the 6th International Conference on Software and Computer Applications, IC- SCA ’17, pp. 62–67. ACM, New York, NY, USA (2017). DOI 10.1145/3056662.3056668
Riyana, S., Riyana, N., Sujinda, W.: An anatomization model for farmer data collections. SN Computer Science 2(5), 1–11 (2021)
Sarwar, B., Karypis, G., Konstan, J., Riedl, J.: Item-based collaborative filtering recommendation algorithms. In: Proceedings of the 10th International Conference on World Wide Web, WWW ’01, pp. 285–295. ACM, New York, NY, USA (2001). DOI 10.1145/371920.372071
Sweeney, L.: K-anonymity: A model for protecting privacy. Int. J. Uncertain. Fuzziness Knowl.-Based Syst. 10(5), 557–570 (2002). DOI 10.1142/S0218488502001648
Ye, Y., Liu, Y., Wang, C., Lv, D., Feng, J.: De-composition: Privacy preservation for multiple sensitive attributes. In: X. Zhou, H. Yokota, K. Deng, Q. Liu (eds.) Database Systems for Advanced Applications, pp. 486–490. Springer Berlin Heidelberg, Berlin, Heidelberg (2009)
Zhang, Q., Koudas, N., Srivastava, D., Yu, T.: Aggregate query answering on anonymized tables. In: 2007 IEEE 23rd International Confer- ence on Data Engineering, pp. 116–125 (2007). DOI 10.1109/ICDE.2007.367857