A New Security Mechanism for Secured Communications Using Steganography and CBA
Main Article Content
Abstract
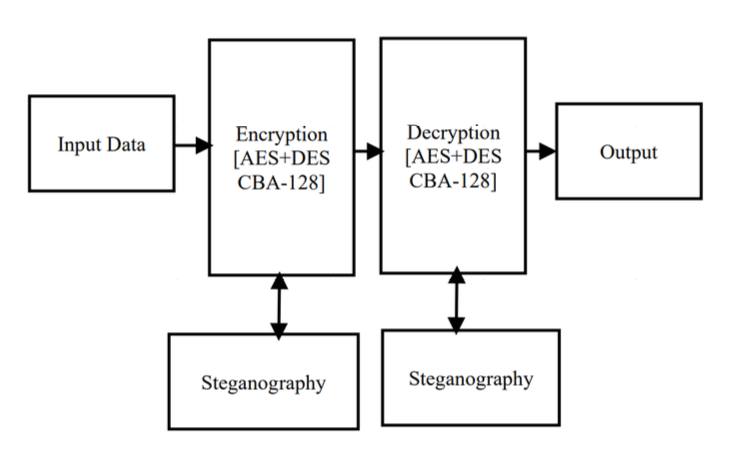
The quick advancement of computerized information trade has caused data security to be of much signicance in information transmission. As a huge measure of information is sent over the Internet, it is fundamental to protect the data from hackers. The current trend is to use AES for safeguarding the data from hackers. Even though, the AES is most frequently used encryption, but it has the disadvantage of employing several direct multi-variation conditions. Hence, it may be broken utilizing mathematical cryptanalysis. Because AES was once considered to be fairly powerful, it has been employed in a variety of encryption schemes, posing a serious threat. This paper proposed a 128-digit key cross breed algorithm (CBA- 128) based on AES and DES for enhancing the security and also applies steganography-based encryption to increase the security of the data during data transmission over the network. The proposed model provides more security for the data to prevent unauthorised access. The experiments conducted to prove the eciency and eectiveness in terms of security level and time.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
References
Pratap Chandra Mandal, “Superiority of the Blowfish Algorithm,” International Journal of Advanced Research in Computer Science and Software Engineering, vol. 2, no.9, pp. 196-201, 2012.
B. AlBelooshi, E. Damiani, K. Salah and T. Martin, “Securing Cryptographic Keys in the Cloud: A Survey,” IEEE Cloud Computing, vol. 3, no. 4, pp. 42-56, 2016.
William Stallings, “The advanced encryption standard,” Cryptologia, vol. 26, No.3, pp 165–188, 2002.
L.Adleman, R.L.Rivest, A.Shamir, and R.L.Rivest, “A Method for Obtaining Digital Signatures and Public-Key Cryptosystems,” ACM Communications, vol. 21, no. 2, pp.120-126, 1978.
Sunil k. Makar, Sombir Singh, and Dr. Sudesh Kumar, “Enhancing the Security of DES Algorithms Using Transposition Cryptography Techniques,” International Journal of Computer Science and Software Engineering, vol. 3, no. 6, pp. 464-470, 2013.
Y. Kun, Z. Han and L. Zhaohui, “An Improved AES Algorithm Based on Chaos,” 2009 International Conference on Multimedia Information Networking and Security, pp. 326-329, 2009.
X. Li, J. Chen, D. Qin and W. Wan, “Research and realization based on hybrid encryption algorithm of improved AES and ECC,” 2010 International Conference on Audio, Language and Image Processing, pp. 396-400, 2010.
M. Zeghid, M. Machhout, L. Khriji, A. Baganne, and R. Tourki, “A Modified AES Based Algorithm for Image Encryption,” World Academy of Science, Engineering and Technology, vol. 27, pp. 206-211, 2007.
A. H. Ali and M. Masrom, “Analysis and implementation of security algorithms for wireless communications,” 2010 The 2nd International Conference on Computer and Automation Engineering (ICCAE), pp. 430-434, 2010.
E. Biham, A. Shamir, “Differential Cryptanalysis of DES-like Cryptosystems,” Journal of Cryptology, vol.4, no. 1, pp. 3–72, 1991.
O. O. Khalifa, M. R. Islam, S. Khan, and M. S. Shebani, “Communications cryptography,” 2004 RF and Microwave Conference, RFM 2004. Proceedings, Selangor, Malaysia, pp. 220-223, 2004.
P. Suthanthiramani, S. Muthurajkumar, G. Sannasi and K. Arputharaj, “Secured data storage and retrieval using elliptic curve cryptography in cloud,” Int. Arab J. Inf. Technol., vol. 18, no. 1, pp. 56-66, 2021.
S. Pradeep, S. Muthurajkumar, S. Ganapathy and A. Kannan, “A Matrix Translation and Elliptic Curve Based Cryptosystem for Secured Data Communications in WSNs,” Wireless Personal Communications, pp.1-20, 2021.
B. Prabhu Kavin and S. Ganapathy, “A secured storage and privacy-preserving model using CRT for providing security on cloud and IoT-based applications,” Computer Networks, vol. 151, pp. 181-190, 2019.
B.P. Kavin and S. Ganapathy, “A new digital signature algorithm for ensuring the data integrity in cloud using elliptic curves,” Int. Arab J. Inf. Technol., vol. 18, no. 2, pp. 180-190, 2021.
B.P. Kavin and S. Ganapathy, “EC(DH)2: an effective secured data storage mechanism for cloud based IoT applications using elliptic curve and Diffie-Hellman,” International Journal of Internet Technology and Secured Transactions, vol. 10, no.5, pp. 601-617, 2020.
B.P Kavin, S.Ganapathy, U.Kanimozhi and A. Kannan, “An enhanced security framework for secured data storage and communications in cloud using ECC, access control and LDSA,” Wireless Personal Communications, vol. 115, no. 2, pp. 1107-1135, 2020.
A.V. Dahat and P.V. Chavan, “Secret Sharing Based Visual Cryptography Scheme Using CMY Color Space,” Procedia Computer Science, vol. 78, pp. 563-570, 2016.
Pratiksha Sethia and V. Kapoor, “A Proposed Novel Architecture for Information Hiding in Image Steganography by using Genetic Algorithm and Cryptography,” Procedia Computer Science, vol. 87, pp. 61 – 66, 2016.
Surinder Kaur, Pooja Bharadwaj and Shivani Mankotia, “Study of Multi-Level Cryptography Algorithm: Multi-Prime RSA and DES,” International Journal of Computer Network and Information Security, vol.9, pp. 22-29, 2017.
Sara Tedmori and Nijad Al-Najdawi,”Lossless Image Cryptography Algorithm Based on Discrete Cosine Transform,” International Arab Journal of Information Technology, vol. 9, no.9, pp. 471-478, 2012.
Jinu Mohan and Rajesh R, “Enhancing home security through visual Cryptography,” Microprocessors and Microsystems, vol. 80, no.103355, pp. 1-13, 2021.
Aesha Elghandour, Ahmad Salah and Abdelrahman Karawia, “A new cryptographic algorithm via a two-dimensional chaotic map,” Ain Shams Engineering Journal, vol.12, no.2, pp.1-14, 2021.
Milad Yousefi Valandar, Peyman Ayubi and Milad Jafari Barani, “A new transform domain steganography based on modified logistic chaotic map for color images,” Journal of Information Security and Applications, vol.34, no. 2, pp. 142-151, 2017.
Milad Yousefi Valandar, Milad Jafari Barani, Peyman Ayubi and Maryam Aghazadeh, “An integer wavelet transform image steganography method based on 3D sine chaotic map,” Multimedia Tools and Applications, Vol.78, pp. 9971–9989, 2019.
Peyman Ayubi, Milad Jafari Barani, Milad Yousefi Valandar, Behzad Yosefnezhad Irani and Reza Sedagheh Maskan Sadigh, “A new chaotic complex map for robust video watermarking,” Artificial Intelligence Review, Vol.54, pp.1237–1280, 2021.
Peyman Ayubi, Saeed Setayeshi and Amir Masoud Rahmani, “Deterministic chaos game: A new fractal based pseudo-random number generator and its cryptographic application,” Journal of Information Security and Applications, vol.52, no. 102472, pp. 1-16, 2020.
O. Osunade and I. A. Ganiyu, “Enhancing the Least Significant Bit (LSB) Algorithm for Steganography,” International Journal of Computer Applications, vol. 149, no. 3, pp. 1-8, 2016.
K. P. B. Madavi and P. V. Karthick, “Enhanced Cloud Security using Cryptography and Steganography Techniques,” 2021 International Conference on Disruptive Technologies for Multi-Disciplinary Research and Applications (CENTCON), pp. 90-95, 2021.
M.Kumar, A.Soni, A.R.S. Shekhawat and A.Rawat, “Enhanced Digital Image and Text Data Security Using Hybrid Model of LSB Steganography and AES Cryptography Technique,” 2022 Second International Conference on Artificial Intelligence and Smart Energy (ICAIS), pp. 1453-1457, 2022.
K.Vandana and S.K. Kumari, “Improving Security with Efficient Key Management in Public cloud using Hybrid AES, ECC and LSB Steganography comparing with Novel hybrid Cube Base Obfuscation,” 2022 International Conference on Business Analytics for Technology and Security (ICBATS), pp. 1-6, 2022.
E.V.Sidi, I.Diop and K.Tall, “A New hybrid approach of Data Hiding Using LSB Steganography and Caesar cipher and RSA algorithm (S-ccr),” 2022 International Conference on Computer Communication and Informatics (ICCCI), 2022, pp. 1-4, 2022.