Hybrid Visual and Optimal Elliptic Curve Cryptography for Medical Image Security in Iot
Main Article Content
Abstract
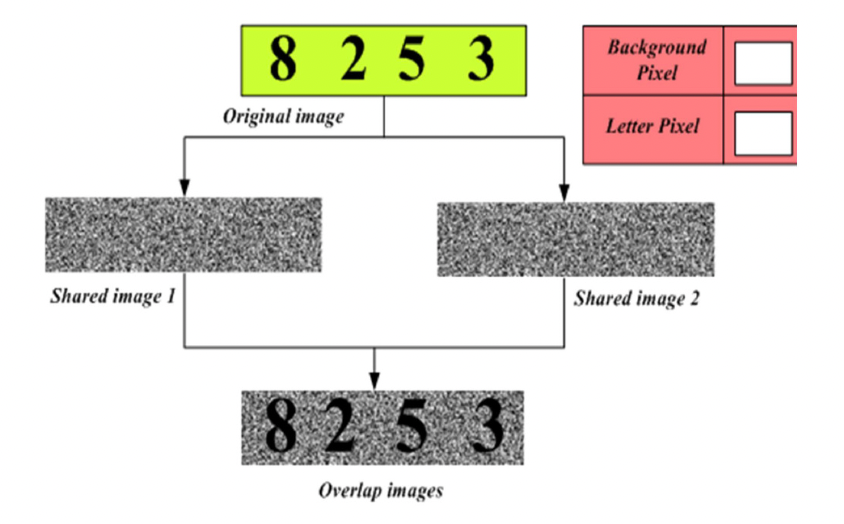
In this manuscript, a hybridizing visual cryptography with Optimal Elliptic Curve Cryptography is proposed for medical image security in Internet of Things (IoT). The visual cryptography is generally used to send the secure and confidential medical image to the receiver. Here, the medical image is transmitted as shares and all shares of the medical image are collectively loaded to retrieve the original medical image. Moreover, the multiple shares are created interms of pixel values of medical image and this share is extracted and partioned in blocks. The blocks of every share are encrypted with elliptic curve cryptography (ECC) mechanisms and encrypted image is decrypted using ECC decrypts. In hybridizing visual crypto with optimal elliptic curve crypto, the optimal key will be generated using an imperialist competitive algorithm. Finally, the decrypted output image compares to the original image. The proposed system is executed on MATLAB platform and performance is evaluated with existing method like Score-based Key Enumeration Algorithm (SKEA). The proposed ESEA approach reduces the file size as 45.76%, 24.97%, 15.86%, 33% and 33.86%.And higher PSNR as 29.08%, 25.86%, 23.98%, 25.86% and 42.75%. The proposed ESEA approach achieves 6.89% higher security than existing SKEA method. Furthermore, the simulation outcome demonstrates that the proposed technique can be able to find the optimal global solutions efficiently and accurately than the existing techniques.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
References
J. Wu, X. Liao and B. Yang, “Color image encryption based on chaotic systems and elliptic curve ElGamal scheme,” Signal Processing, vol. 141, pp. 109-124, 2017.
S. Li, L. Xu and S. Zhao, “5G Internet of Things: A survey,” Journal of Industrial Information Integration, vol. 10, pp. 1-9, 2018.
S. Mythili, K. Thiyagarajah, P. Rajesh and F.H. Shajin , “Ideal position and size selection of unified power flow controllers (UPFCs) to upgrade the dynamic stability of systems: an antlion optimiser and invasive weed optimisation algo- rithm,” HKIE Trans, vol. 27, no.1, pp. 25-37, 2020.
M. Conti, A. Dehghantanha, K. Franke and S. Watson, “Internet of Things security and forensics: Challenges and opportunities,” Future Generation Computer Systems, vol. 78, pp. 544-546, 2018.
P. Rajesh and F. H. Shajin, “A Multi-Objective Hybrid Algorithm for Planning Electrical Distribution System,” European Journal of Electrical Engineering, vol.22, no.4-5, pp.377-387, 2020.
M. Wollschlaeger, T. Sauter and J. Jasperneite, “The Future of Industrial Communication: Automation Networks in the Era of the Internet of Things and Industry 4.0,” IEEE Industrial Electronics Magazine, vol. 11, no. 1, pp. 17-27, 2017.
FH. Sha jin,P. Ra jesh. “Trusted secure geographic routing protocol: outsider attack detection in mobile ad hoc networks by adopting trusted secure geographic routing protocol,” International Journal of Pervasive Computing and Communications, 2020.
F. Alaba, M. Othman, I. Hashem and F. Alotaibi, “Internet of Things security: A survey,” Journal of Network and Computer Applications, vol. 88, pp. 10-28, 2017.
M. Mahdavinejad, M. Rezvan, M. Barekatain, P. Adibi, P. Barnaghi and A. Sheth, “Machine learning for internet of things data analysis: a survey,” Digital Communications and Networks, vol. 4, no. 3, pp. 161-175, 2018.
MK. Thota, FH. Shajin and P. Rajesh. “Survey on software defect prediction techniques,” International Journal of Applied Science and Engineering, vol.17, no.4, pp.331-44, 2020;
G. Akpakwu, B. Silva, G. Hancke and A. Abu- Mahfouz, “A Survey on 5G Networks for the Internet of Things: Communication Technologies and Challenges,” IEEE Access, vol. 6, pp. 3619- 3647, 2018.
D. Boubiche, S. Athmani, S. Boubiche and H. Toral-Cruz, “Cybersecurity Issues in Wireless Sensor Networks: Current Challenges and Solutions,”Wireless Personal Communications, 2020.
S. Bitam, S. Zeadally and A. Mellouk, “Bio- inspired cybersecurity for wireless sensor networks,” IEEE Communications Magazine, vol. 54, no. 6, pp. 68-74, 2016.
U. Satija, B. Ramkumar and M. Sabarimalai Manikandan, “Real-Time Signal Quality-Aware ECG Telemetry System for IoT-Based Health Care Monitoring,” IEEE Internet of Things Journal, vol. 4, no. 3, pp. 815-823, 2017.
R. Riyaldhi, Rojali and A. Kurniawan, “Improvement of Advanced Encryption Standard Algorithm With Shift Row and S.Box Modification Mapping in Mix Column,” Procedia Computer Science, vol. 116, pp. 401-407, 2017.
L. Handoko, C. Umam, D. Setiadi and E. Rachmawanto, “DIGITAL SIGNATURE PADA CITRA MENGGUNAKAN RSA DAN VIGENERE CIPHER BERBASIS MD5,” Simetris: JurnalTeknikMesin, ElektrodanIlmuKomputer, vol. 10, no. 1, pp. 357-366, 2019.
M. Elhoseny, K. Shankar, S. Lakshmanaprabu, A. Maseleno and N. Arunkumar, “Hybrid optimization with cryptography encryption for medical image security in Internet of Things,” Neural Computing and Applications, vol. 32, no. 15, pp. 10979-10993, 2018.
X. Cheng et al., “Secure Identity Authentication of Community Medical Internet of Things,” IEEE Access, vol. 7, pp. 115966-115977, 2019.
R. Baashirah and A. Abuzneid, “SLEC: A Novel Serverless RFID Authentication Protocol Based on Elliptic Curve Cryptography,” Electronics, vol. 8, no. 10, p. 1166, 2019.
A. Ostad-Sharif, D. Abbasinezhad-Mood and M. Nikooghadam, “Efficient utilization of elliptic curve cryptography in design of a three-factor authentication protocol for satellite communications,” Computer Communications, vol. 147, pp. 85-97, 2019.
N. Singh, A. Hans and S. Kaur, “Layer and RFID Based Security Issues of Internet of Things,” International Journal of Grid and Distributed Computing, vol. 9, no. 10, pp. 301-310, 2016.
S. Kalsi, H. Kaur and V. Chang, “DNA Cryptography and Deep Learning using Genetic Algorithm with NW algorithm for Key Generation,” Journal of Medical Systems, vol. 42, no. 1, 2017.
M. Elhoseny, K. Shankar, S. Lakshmanaprabu, A. Maseleno and N. Arunkumar, “Hybrid optimization with cryptography encryption for medical image security in Internet of Things,” Neural Computing and Applications, vol. 32, no. 15, pp. 10979-10993, 2018.
Y. Guan and X. Ge, “Distributed Secure Estimation Over Wireless Sensor Networks Against Random Multichannel Jamming Attacks,” IEEE Access, vol. 5, pp. 10858-10870, 2017.
T. Avudaiappan, R. Balasubramanian, S.S., Pandiyan, M.Saravanan, S.K.. Lakshmanaprabu and K., Shankar, “Medical image security us- ing dual encryption with oppositional based optimization algorithm,” Journal of medical systems, vol.42, no.11, pp.1-11, 2018.
A. Banik, Z. Shamsi and D.S. Laiphrakpam, “An encryption scheme for securing multiple medical images,” Journal of Information Security and Applications, vol. 49, p.102398, 2019.
R. Hamza, Z. Yan, K. Muhammad, P. Bellav- ista and F. Titouna, “A privacy-preserving cryptosystem for IoT E-healthcare,” Information Sciences, vol. 527, pp. 493-510, 2020.
M. Khari, A. Garg, A. Gandomi, R. Gupta, R. Patan and B. Balusamy, “Securing Data in Internet of Things (IoT) Using Cryptography and Steganography Techniques,” IEEE Transactions on Systems, Man, and Cybernetics: Systems, vol. 50, no. 1, pp. 73-80, 2020.
S. Koppu and V. Viswanatham, “Medical image security enhancement using two dimensional chaotic mapping optimized by self-adaptive grey wolf algorithm,” Evolutionary Intelligence, vol. 11, no. 1-2, pp. 53-71, 2018.
K. Shankar, M. Elhoseny, E. Perumal, M. Ila- yaraja and K.S. Kumar, “An efficient image encryption scheme based on signcryption technique with adaptive elephant herding optimization,” in Cybersecurity and Secure Information Systems, pp. 31-42, 2019 Springer, Cham.
K. Shankar, M. Elhoseny, R.S. Kumar, S.K. Lakshmanaprabu and X. Yuan, “Secret image sharing scheme with encrypted shadow images using optimal homomorphic encryption technique,” Journal of Ambient Intelligence and Humanized Computing, vol.11, no.5, pp.1821-1833, 2020.
A. Sivasankari and S. Krishnaveni, “Optimal Wavelet Coefficients Based Steganography for Image Security with Secret Sharing Cryptography Model,” in Cybersecurity and Secure Information Systems, Springer, Cham, pp. 67-85, 2019.
R. Villanueva-Polanco, “A comprehensive study of the key enumeration problem,” Entropy, vol.21, no.10, p.972, 2019