Application of an Analytic Hierarchy Process to Select the Level of a Cyber Resilient Capability Maturity Model in Digital Supply Chain Systems
Main Article Content
Abstract
Cyber resilient is the ability to prepare for, respond to and recover from cyber attacks. Cyber resilient has emerged over the past few years because traditional cybersecurity measures are no longer enough to protect organizations from the spate of persistent attacks. It helps an organization protect against cyber risks, defend against and limit the severity of attacks, and ensure its continued survival despite an attack.
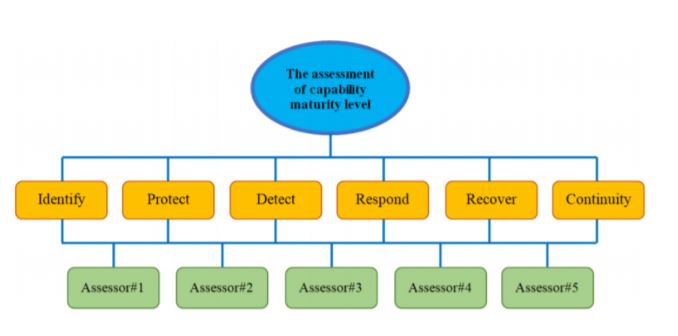
The cyber resilient capability maturity model is a very important element within an effective in digital supply chain. The maturity model has 6 components: identify, protect, detect, respond, recover and continuity which affect the cybersecurity of the organization. To measure the maturity level needs a holistic approach. Therefore, the analytic hierarchy process (AHP) approach which allows both multi-criteria and simultaneous evaluation. Generally, the factors affecting cyber resilient in digital supply chain have non-physical structures. Therefore, the real problem can be represented in a better way by using fuzzy numbers instead of numbers to evaluate these factors.
In this study, a fuzzy AHP approach is proposed to determine the cyber resilient capability maturity level in digital supply chain. The proposed method is applied in a real SMEs company. In the application, factors causing are weighted with triangular fuzzy numbers in pairwise comparisons. The result indicate that the weight factors from comparing the relationship of all factors put the importance of identify factors first, followed by protect, detect, respond, recover and continuity respectively.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
References
M. Warren, and W. Hutchinson, “Cyber attacks against supply chain management systems: a short note,” International Journal of Physical Distribution & Logistics Management, vol. 30 Iss. 7/8, pp.710 -716, 2000.
C.W. Zobel, and L. Khansa, “Quantifying Cyberinfrastructure Resilience against Multi-Event Attacks,” Decision Sciences, vol.43, no.4, pp.687-710, 2012.
M. Levi, “Assessing the trends, scale and nature of economic cybercrimes: overview and Issues,” Crime, Law and Social Change, vol.67, no.1, pp.3-20, 2016.
H.S. Brar, and G. Kumar, “Cybercrimes: A Proposed Taxonomy and Challenges,” Journal of Computer Networks and Communications, 2018.
T. Rusi, and M. Lehto, “Cyber threats mega trends in cyber space,” In ICMLG 2017 5th International Conference on Management Leadership and Governance. Academic Conferences and Publishing Limited, p. 323, 2017.
B. Gaudenzi, and G. Siciliano, “Managing IT and Cyber Risks in Supply Chains,” Supply Chain Risk Management, pp. 85–96, 2017.
S. Papastergiou, and N. Polemi, “MITIGATE: A dynamic supply chain cyber risk assessment methodology,” In Smart Trends in Systems, Security and Sustainability, pp.1-9, Springer, Singapore, 2018.
G. Büyüközkan, and F. Göçer, “Digital Supply Chain: Literature review and a proposed framework for future research,” Computers in Industry, vol.97, pp.157–177, 2018.
I. Dmitry, D. Alexandre, and S. Boris, “The impact of digital technology and Industry 4.0 on the ripple effect and supply chain risk analytics,” International Journal of Production research, vol.57, no. 3, pp.829-846, 2019.
Humphrey, Cmm, IEEE, vol.1, 1989.
P.D. Curtis, and N. Mehravari, “Evaluating and improving cybersecurity capabilities of the energy critical infrastructure,” In Technologies for Homeland Security (HST), 2015 IEEE International Symposium, pp. 1–6, 2015.
K. Boonsita Kitisrivorapot, “Selection of Logistics Service Providers for Hana Microelectronics Public Company Limited, the Northern Region Industrial Estate, by Applying Analytic Hierarchy Process and Fuzzy Set Theory for Decision Making,” Graduate School, Chiang mai University, 2011.
M. Phayung, “Fuzzy Systems and Neural Network,” Faculty of Information Technology, King Mongkut’s University of Technology North Bangkok, 2011.
Yasemin, and F.G. Wu, “Global supplier selection: a fuzzy-AHP approach,” International Journal of Production Research, vol.46, pp.3825-3857, 2004.
Y.C. Erensal, T. O¨ zcan, and M.L. Demircan, “Determining key capabilities in technology management using fuzzy analytic hierarchy process: A case study of Turkey,” Information Sciences, vol. 176, pp. 2755–2770, 2006.
D.Y. Chang, “Applications of the extent analysis method on fuzzy AHP,” European Journal of Operational Research, vol.95, pp.649–655, 1996.
D.Y. Chang, “Extent Analysis and Systematic Decisin, Optimization Techniques and Application,” World Sciencific, Singapore, p.352, 1992.
Framework for Improving Critical Infrastructure Cybersecurity version 1.1. National Institute of Standards and Technology. Available at: https://doi.org/10.6028/NIST.CSWP.04162018 [Accessed:25/11/19].
J.W. Candra, O.C. Briliyant, and S.R. Tamba, “ISMS planning based on ISO/IEC 27001:2013 using analytical hierarchy process at gap analysis phase (Case study : XYZ institute),” 2017 11th International Conference on Telecommunication Systems Services and Applications (TSSA). IEEE, 2017.
M.I. Tariq, and S. Vito, “Analysis of ISO 27001: 2013 Controls Effectiveness for Cloud Computing.” International Conference on Information Systems Security and Privacy. Vol. 2. SCITEPRESS, 2016.
J. Gutiérrez-Martínez, M. A. Núñez-Gaona, and H. Aguirre-Meneses, “Business Model for the rity of a Large-Scale PACS, Compliance with ISO/27002:2013 Standard,” Journal of Digital Imaging, vol.28, no.4.
E. Humphreys, “The Future Landscape of ISMS Standards,” Datenschutz und Datensicherheit-DuD, vol. 42, no.7, pp: 421-423, 2018.
S.V. Aleksandrova, M.A. Aleksandrov, and V.A. Vasiliev, “Business Continuity Management System,” 2018 IEEE International Conference" Quality Management, Transport and Information Security, Information Technologies"(IT&QM&IS). IEEE, 2018.
Y. Muflihah, and P.S. Apol, “A basic element of it business continuity plan: systematic.” Jurnal Informatika, vol.12, no.1, pp.-17-23, 2018.
R. Koen, S. R. Von, and M. Gerber, “ ICT Readiness for Business Continuity in local government,” 2016 IST-Africa Week Conference, 2016.
J. Meszaros, and A. Buchalcevova, “Introducing OSSF: A framework for online service cybersecurity risk management,” Computers & Security, vol.65, pp.300–31, 2017.
M.F. Blos, S. L. Hoeflich, E.M. Dias, and H.-M. Wee, “A note on supply chain risk classification: discussion and proposal,” International Journal of Production Research, vol.54, no.5, pp.1568–1569, 2015.
S. Papastergiou, and N. Polemi, “MITIGATE: A Dynamic Supply Chain Cyber Risk Assessment Methodology,” Smart Trends in Systems, Security and Sustainability, pp.1–9, 2017.
M.F. Blos, and S.L. Hoeflich, “Supply chain risk management framework for virtual enterprises: a theoretical approach,” Unisanta Science and Technology, vol.5, no.3, pp.161-166, 2017.
D. Proenca, J. Estevens, R. Vieira, and J. Borbinha, “Risk Management: A Maturity Model Based on ISO 31000,” 2017 IEEE 19th Conference on Business Informatics (CBI), 2017.
U.R. De Oliveira, F.A.S. Marins, H.M. Rocha, and V.A.P., Salomon, V. A. P., “The ISO 31000 standard in supply chain risk management,” Journal of Cleaner Production, vol.151, pp.616–633, 2017.
B. Massimino, J.V. Gray, and Y. Lan, “On the Inattention to Digital Confidentiality in Operations and Supply Chain Research.” Production and Operations Management, vol. 27, no,,pp. 1492–1515, 2018.
A. Yeboah-Ofori, and S. Islam, “Cyber Security Threat Modeling for Supply Chain Organizational Environments,” Future Internet, vol.11, no.3, pp.1-25, 2019.