Hybrid Machine Learning: A Tool to Detect Phishing Attacks in Communication Networks
Main Article Content
Abstract
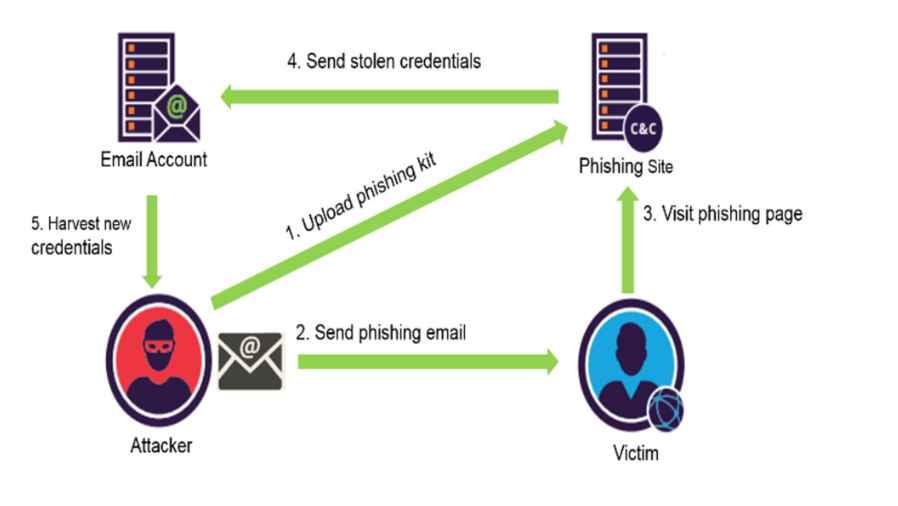
Phishing is a cyber-attack that uses disguised email as a weapon and has been on the rise in recent times. Innocent Internet user if peradventure clicking on a fraudulent link may cause him to fall victim of divulging his personal information such as credit card pin, login credentials, banking information and other sensitive information. There are many ways in which the attackers can trick victims to reveal their personal information. In this article, we select important phishing URLs features that can be used by attacker to trick Internet users into taking the attacker’s desired action. We use two machine learning techniques to accurately classify our data sets. We compare the performance of other related techniques with our scheme. The results of the experiments show that the approach is highly effective in detecting phishing URLs and attained an accuracy of 97.8% with 1.06% false positive rate, 0.5% false negative rate, and an error rate of 0.3%. The proposed scheme performs better compared to other selected related work. This shows that our approach can be used for real-time application in detecting phishing URLs.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
References
E. Soegoto and M. Rafi, "Internet role in improving business transaction," in Proceedings of the IOP Conference Series: Materials Science and Engineering, p.012059, 2018.
M. Graham and W. H. Dutton, Society and the internet: How networks of information and communication are changing our lives: Oxford University Press, 2019.
Miniwatts Marketing Group. (2019, November 11,). Internet World Starts. Available: https://www.internetworldstats.com/stats.htm
M. Büchi, N. Just, and M. Latzer, "Caring is not enough: the importance of Internet skills for online privacy protection," Information, Communication & Society, Vol.20, No.8, pp. 1261-1278, 2017.
A. Wang, W. Chang, S. Chen, and A. Mohaisen, "Delving into internet ddos attacks by botnets: Characterization and analysis," IEEE/ACM Transactions on Networking (TON), Vol.26, No.6, pp. 2843-2855, 2018.
J. A. Chaudhry, S. A. Chaudhry, and R. G. Rittenhouse, "Phishing attacks and defenses," International Journal of Security and Its Applications, Vol.10, No.1, pp. 247-256, 2016.
APWG. (2019, November 13, ). Anti-Phishing Working Group Phishing Activity Trends Report. Available: https://docs.apwg.org/reports/apwg_trends_report_q2_2019.pdf
J. Hong, "The current state of phishing attacks," 2012.
A. Bouveret, Cyber risk for the financial sector: a framework for quantitative assessment: International Monetary Fund, 2018.
Kaspersky. (2019, November 25). How to protect yourself against spam email and phishing. Available: https://www.kaspersky.co.za/resource-center/threats/spam-phishing
K. L. Chiew, K. S. C. Yong, and C. L. Tan, "A survey of phishing attacks: their types, vectors and technical approaches," Expert Systems with Applications, Vol.106, pp. 1-20, 2018.
L. Lazar. (2020, 20 October). Our Analysis of 1,019 Phishing Kits. Available: https://www.imperva.com/blog/our-analysis-of-1019-phishing-kits/
V. Suganya, "A review on phishing attacks and various anti phishing techniques," International Journal of Computer Applications, Vol.139, No.1, pp. 20-23, 2016.
L.-H. Lee, K.-C. Lee, H.-H. Chen, and Y.-H. Tseng, "Poster: Proactive blacklist update for anti-phishing," in Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, pp.1448-1450, November 2014.
L. Li, E. Berki, M. Helenius, and S. Ovaska, "Towards a contingency approach with whitelist-and blacklist-based anti-phishing applications: what do usability tests indicate?," Behaviour & Information Technology, Vol.33, No.11, pp. 1136-1147, 2014.
M. Aburrous, M. A. Hossain, K. Dahal, and F. Thabtah, "Intelligent phishing detection system for e-banking using fuzzy data mining," Expert systems with applications, Vol.37, No.12, pp. 7913-7921, 2010.
R. B. Basnet, A. H. Sung, and Q. Liu, "Learning to detect phishing URLs," International Journal of Research in Engineering and Technology, Vol.3, No.6, pp. 11-24, 2014.
A. Jain and V. Richariya, "Implementing a web browser with phishing detection techniques," arXiv preprint arXiv:1110.0360, 2011.
M. A. Mahmood and L. Rajamani, "APD: ARM Deceptive Phishing Detector System Phishing Detection in Instant Messengers Using Data Mining Approach " Global Trends in Computing and Communication Systems, Vol.269, No.1, pp. 490-502, 2011.
M. Ajlouni, W. e. Hadi, and J. Alwedyan, "Detecting phishing websites using associative classification," image, Vol.5, No.23, pp. 36-40, 2013.
D. Zhang, Z. Yan, H. Jiang, and T. Kim, "A domain-feature enhanced classification model for the detection of Chinese phishing e-Business websites," Information & Management, Vol.51, No.7, pp. 845-853, 2014.
M. Moghimi and A. Y. Varjani, "New rule-based phishing detection method," Expert systems with applications, Vol.53, pp. 231-242, 2016.
G. Ramesh, I. Krishnamurthi, and K. S. S. Kumar, "An efficacious method for detecting phishing webpages through target domain identification," Decision Support Systems, Vol.61, pp. 12-22, 2014.
A. K. Jain and B. B. Gupta, "A machine learning based approach for phishing detection using hyperlinks information," Journal of Ambient Intelligence and Humanized Computing, Vol.10, No.5, pp. 2015-2028, 2019.
E. Gandotra and D. Gupta, "An Efficient Approach for Phishing Detection using Machine Learning," in Multimedia Security, ed: Springer, 2021, pp. 239-253.
L. M. Ellram and W. L. Tate, "The use of secondary data in purchasing and supply management (P/SM) research," Journal of purchasing and supply management, Vol.22, No.4, pp. 250-254, 2016.
PhishTank. (2019, November 25,). Statistics about phishing activity and PhishTank usage. Available: http://www.phishtank.com/stats.php
R. B. Basnet, A. H. Sung, and Q. Liu, "Feature selection for improved phishing detection," in Proceedings of the International Conference on Industrial, Engineering and Other Applications of Applied Intelligent Systems, pp.252-261, 2012.
H. N. Security. (2019). Phishing attacks at highest level in three years. Available: https://www.helpnetsecurity.com/2019/11/07/phishing-attacks-levels-rise/
J. LaCour, "Phishing Trends and Intelligent Report," 2019.
R. Verma and A. Das, "What's in a url: Fast feature extraction and malicious url detection," in Proceedings of the Proceedings of the 3rd ACM on International Workshop on Security and Privacy Analytics, pp.55-63, 2017.
S. Wedyan and F. Wedyan, "An Associative Classification Data Mining Approach for Detecting Phishing Websites," Journal of Emerging Trends in Computing and Information Sciences, Vol.4, No.12, 2013.
S. Le Page, G.-V. Jourdan, G. v. Bochmann, J. Flood, and I.-V. Onut, "Using url shorteners to compare phishing and malware attacks," in Proceedings of the 2018 APWG Symposium on Electronic Crime Research (eCrime), pp.1-13, 2018.
L. James, Phishing exposed. Canada.: Syngress, 2005.