Boundary Bit: Architectural Bound Checking for Buffer-Overflow Protection
Main Article Content
Abstract
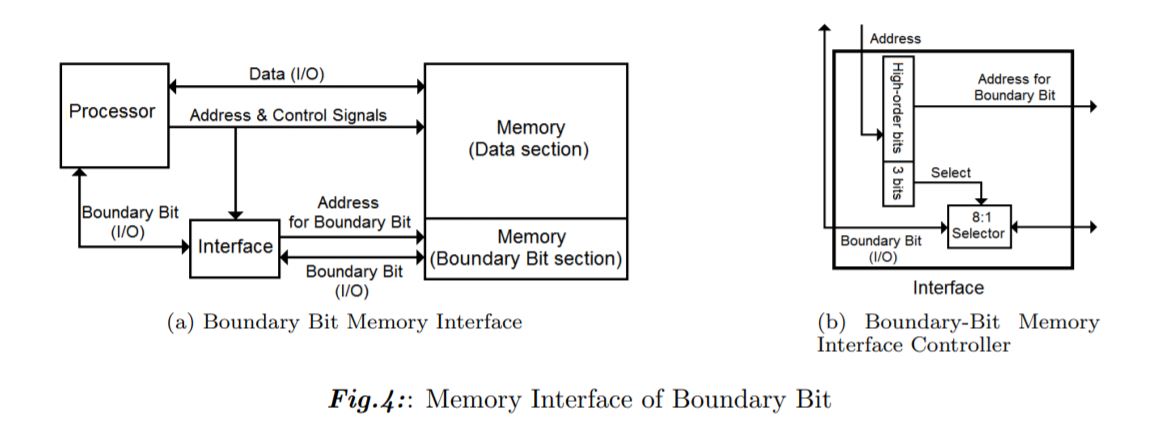
We propose Boundary Bit, a new architectural bound-checking approach that detects and prevents buffer overflow attacks. Boundary Bit extends an architecture by associating a bit to each memory entry. Software can set a (boundary) bit to delimit an object. On each memory access, the hardware will dynamically validate the object's bound using the boundary bit. With minimal hints from the compiler, our architectural design eliminates most (if not all) types of buffer-overflow attacks. These include attacks on non-control data (variables and arguments) and array-indexing errors. We evaluate the performance of Boundary Bit using simulation, and the results show that the majority of performance overheads lies in bit scanning operations. To mitigate performance overheads, we introduce a hardware bitmap to act as a cache. The results from our simulation shows that the hardware bitmap can absorb most overhead from bit scanning, which in the best-case scenario translated to 30 times speed up compared to the version that does not utilize bitmap cache.
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.
References
P. Akritidis, M. Costa, M. Castro, and S. Hand, “Baggy bounds checking: An efficient and backwards-compatible defense against outof-bounds errors,” in 18th USENIX Security Symposium (USENIX Security ’09), pp.1-10, USENIX, August 2009.
M. Bishop, S. Engle, D. Howard and S. Whalen, “A Taxonomy of Buffer Overflow Characteristics,” in IEEE Transactions on Dependable and Secure Computing, vol. 9, no. 3, pp. 305-317, May-June 2012.
M. Chabbi, S. Perianayagam, G. Andrews, and S. Debray, “Efficient dynamic taint analysis using multicore machines,” Report, The University of Arizona, 2007.
S. Chiamwongpaet and K. Piromsopa, “The implementation of Secure Canary Word for bufferoverflow protection,” 2009 IEEE International Conference on Electro/Information Technology, Windsor, ON, 2009, pp. 56-61.
S. Chiamwongpaet, Buffer-overflow Protection using Boundary Bit, Thesis, 2017.
C. Cowan, S. Beattie, J. Johansen, and P. Wagle, “PointguardTM: protecting pointers from buffer overflow vulnerabilities,” in Proceedings of the 12th conference on USENIX Security Symposium, vol.12, pp. 7, 1251360.USENIX Association, August 2003.
C. Cowan, C. Pu, D. Maier, H. Hintony, J. Walpole, P. Bakke, S. Beattie, A. Grier, P. Wagle, and Q. Zhang, “Stackguard: automatic adaptive detection and prevention of bufferoverflow attacks,” in Proceedings of the 7th conference on USENIX Security Symposium, vol. 7, pp. 5, 1267554. USENIX Association, January 1998.
U. Dhawan, C. Hritcu, R. Rubin, N. Vasilakis, S. Chiricescu, J. M. Smith, T. F. Knight, Jr., B. C. Pierce, and A. DeHon, “Architectural support for software-defined metadata processing,” in Proceedings of the Twentieth International Conference on Architectural Support for Programming Languages and Operating Systems, ASPLOS ’15, pp. 487–502, New York, NY, USA, 2015. ACM.
D. Dhurjati and V. Adve, “Backwardscompatible array bounds checking for c with very low overhead,” in Proceedings of the 28th International Conference on Software Engineering, ICSE ’06, pp. 162–171, New York, NY, USA, 2006. ACM.
Nicolas Economou. Microsoft windows up to 8.1 memory object win32k.sys buffer overflow. http://www.scip.ch/en/?vuldb.11444, 04/07/2017 2013.
Agner Fog. Instruction tables. http://www. agner.org/optimize/instructiontables. pdf, 2017-05-02 2017.
Edward F. Gehringer and J. Leslie Keedy, “Tagged architecture: how compelling are its advantages?,” SIGARCH Comput. Archit. News, vol.13, no.3, pp.162–170, June 1985.
R. Gil, The undefined quest for full memory safety, Thesis, 2017.
E. Haugh, “Testing c programs for buffer overflow vulnerabilities,” in Proceedings of the Network and Distributed System Security Symposium, pp. 123–130, 2003.
Richard W M Jones and Paul H J Kelly, “Backwards-compatible bounds checking for arrays and pointers in c programs,” in Distributed Enterprise Applications. HP Labs Tech Report, pp. 255–283, 1997.
S. Kaufer, R. Lopez, and S. Pratap, “Saber-C — an interpreter-based programming environment for the C language,” in USENIX Association, editor, Summer USENIX Conference Proceedings, pp. 161–171, Berkeley, CA, USA, Summer 1988. USENIX.
A. Kwon, U. Dhawan, J. M. Smith, T. F. Knight, G. Bioworks, and A. Dehon, “Low-fat pointers: compact encoding and efficient gate-level implementation of fat pointers for spatial safety and capability-based security,” CCS’13: Proceedings of the 2013 ACM SIGSAC conference on Computer & communications security, pp.721-732, November 2013.
J. L. Steffen, “Adding run-time checking to the portable c compiler,” Software: Practice and Experience, vol.22, issue 4, pp.305–316, April 1992.
K. Lhee and S. J. Chapin, “Buffer overflow and format string overflow vulnerabilities,” Software: Practice and Experience, vol.33, issue 5, pp.423–460, April 2003.
D. Li, Z. Liu, and Y. Zhao, “Heapdefender: A mechanism of defending embedded systems against heap overflow via hardware,” in 2012 9th International Conference on Ubiquitous Intelligence and Computing and 9th International Conference on Autonomic and Trusted Computing, pp. 851–856, 2012.
A. Maia, L. Melo, F. M. Q. Pereira, O. P. V. Neto, and L. B. Oliveira, “Smov: Array bound- Boundary Bit: Architectural Bound Checking for Buffer-Overflow Protection 173 check and access in a single instruction,” in 2016 13th IEEE Annual Consumer Communications Networking Conference (CCNC), pp. 745–751, Jan 2016.
Sean Dillon (Microsoft). Microsoft windows up to server 2016 smb buffer overflow. https:// vuldb.com/?id.98018,07/14/2017 2017.
S. Nagarakatte, J. Zhao, M. M.K. Martin, and S. Zdancewic, “Softbound: Highly compatible and complete spatial memory safety for c.,” in Proceedings of the 30th ACM SIGPLAN Conference on Programming Language Design and Implementation, PLDI ’09, pp. 245–258, New York, NY, USA, 2009. ACM.
S. Nagarakatte, J. Zhao, M. M.K. Martin, and S. Zdancewic, “Cets: Compiler enforced temporal safety for c,” in Proceedings of the 2010 International Symposium on Memory Management, ISMM ’10, pp. 31–40, New York, NY, USA, 2010. ACM.
Elliot I. Organick. A programmer’s view of the Intel 432 system. McGraw-Hill, Inc., 1983.
H. Patil and C. Fischer, “Low-cost, concurrent checking of pointer and array accesses in c programs,” Software—Practice & Experience, vol.27, issue 1, pp.87–110, January 1997.
K. Piromsopa and R. J. Enbody, “Secure Bit: Transparent, Hardware Buffer-Overflow Protection,” in IEEE Transactions on Dependable and Secure Computing, vol. 3, no. 4, pp. 365-376, Oct.-Dec. 2006
K. Piromsopa, SECURE BIT: BUFFEROVERFLOW PROTECTION, Thesis, 2006.
K. Piromsopa and S. Chiamwongpaet, “Secure Bit Enhanced Canary: Hardware Enhanced Buffer-Overflow Protection,” 2008 IFIP International Conference on Network and Parallel Computing, Shanghai, 2008, pp. 125-131.
K. Piromsopa and R. J. Enbody, “Architecting security: A secure implementation of hardware buffer-overflow protection,” in Proceedings of the Third Conference on IASTED International Conference: Advances in Computer Science and Technology, ACST’07, pp. 17–22, USA, 2007. ACTA Press.
K. Piromsopa and R. J. Enbody, “Survey of protections from buffer-overflow attacks,” Engineering Journal, vol.5, no.2, pp.31–52, Feb. 2011.
O. Ruwase and M. S. Lam, “A practical dynamic buffer overflow detector,” in Proceedings of the 11th Annual Network and Distributed System Security Symposium, pp. 159–169, 2004.
M. S. Kirkpatrick, Canary bit: Extending secure bit for data pointer protection from buffer overflow attacks, Thesis, 2007.
L. K. Sah, S. A. Islam and S. Katkoori, “An Efficient Hardware-Oriented Runtime Approach for Stack-based Software Buffer Overflow Attacks,” 2018 Asian Hardware Oriented Security and Trust Symposium (AsianHOST), Hong Kong, 2018, pp. 1-6.
Charles Schmidt and Tom Darby. The what, why, and how of the 1988 internet worm. http: //www.snowplow.org/tom/worm/worm.html, 1988.
Z. Shao, Q. Zhuge, Y. He and E. H. -. Sha, “Defending embedded systems against buffer overflow via hardware/software,” 19th Annual Computer Security Applications Conference, 2003. Proceedings., Las Vegas, NV, USA, 2003, pp. 352-361.
Tzi-Cker Chiueh and Fu-Hau Hsu, “RAD: a compile-time solution to buffer overflow attacks,” Proceedings 21st International Conference on Distributed Computing Systems, Mesa, AZ, USA, 2001, pp. 409-417.
D. W. Plater, Y. Yesha and E. K. Park, “Extensions to the c programming language for enhanced fault detection,” Software: Practice and Experience, vol.23, issue 6, pp.617–628, June 1993.
D. Wagner, J. S. Foster, E. A. Brewer, and A. Aiken, “A first step towards automated detection of buffer overrun vulnerabilities,” in NETWORK AND DISTRIBUTED SYSTEM SECURITY SYMPOSIUM, pp.3–17, 2000.
Webopedia. buffer overflow. http://www. webopedia.com/TERM/B/bueroverow.html.
M.V. Zelkowitz, Paul R. McMullin, Keith R. Merkel, and Howard J. Larsen, “Error checking with pointer variables,” in Proceedings of the 1976 Annual Conference, ACM ’76, pp. 391–395, New York, NY, USA, 1976. ACM.